Access to a 3scale Account
Access to a Red Hat SSO installation
An API client. We assume it to be Postman client for Chrome
Your RHEL box IP, refered to rhel-box-ip. We assume RHSSO and 3scale on Prem are runnning on the same RHEL box with this IP. (If not substitute as appropriate below).
Note: We have inserted whitespace in some URLs as they contain placeholders and are not valid URLs as they appear. Insert the values resolving to the URL fragments and remove whitespace.
Go to API - Integration and click edit integration settings
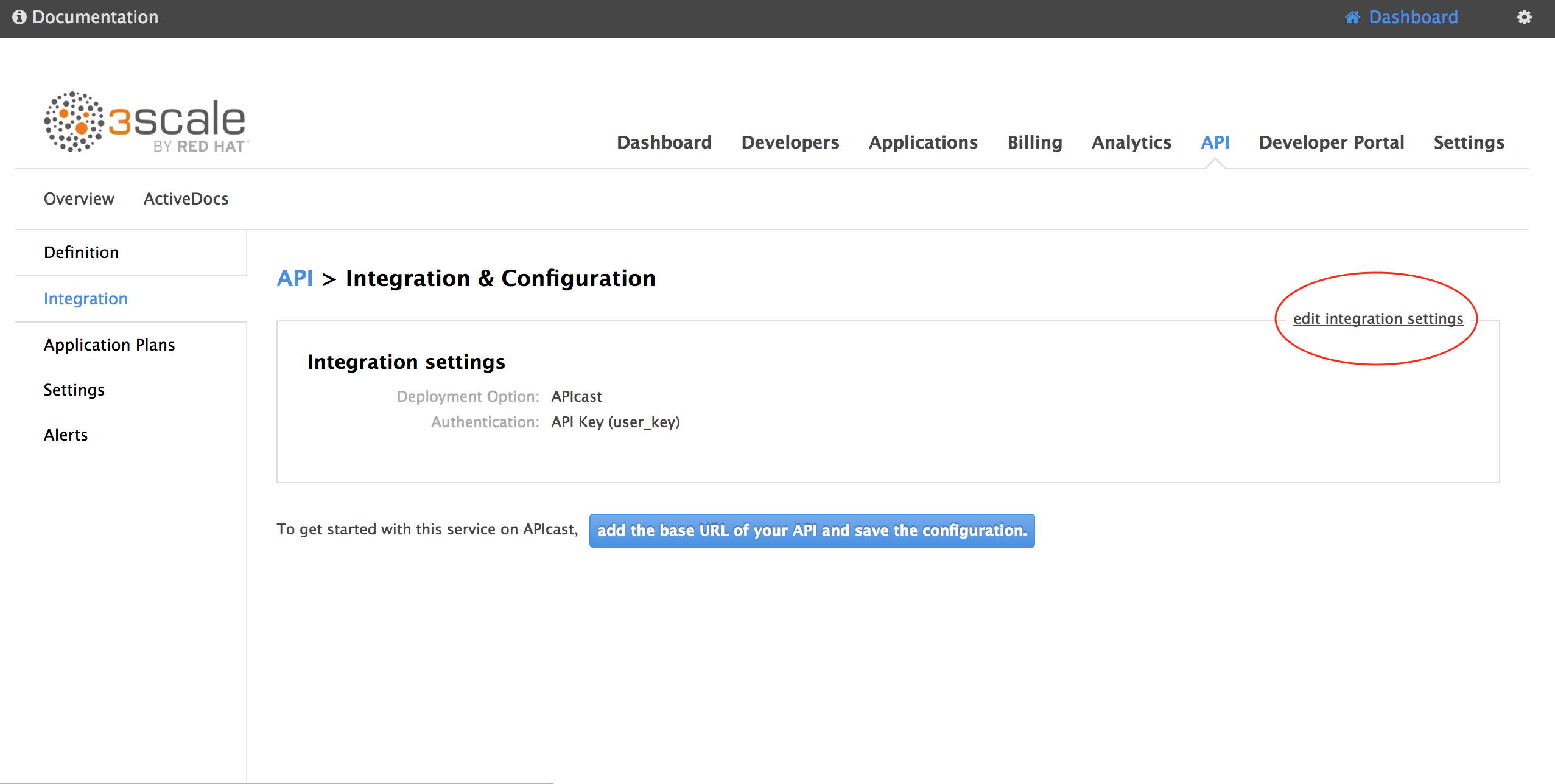
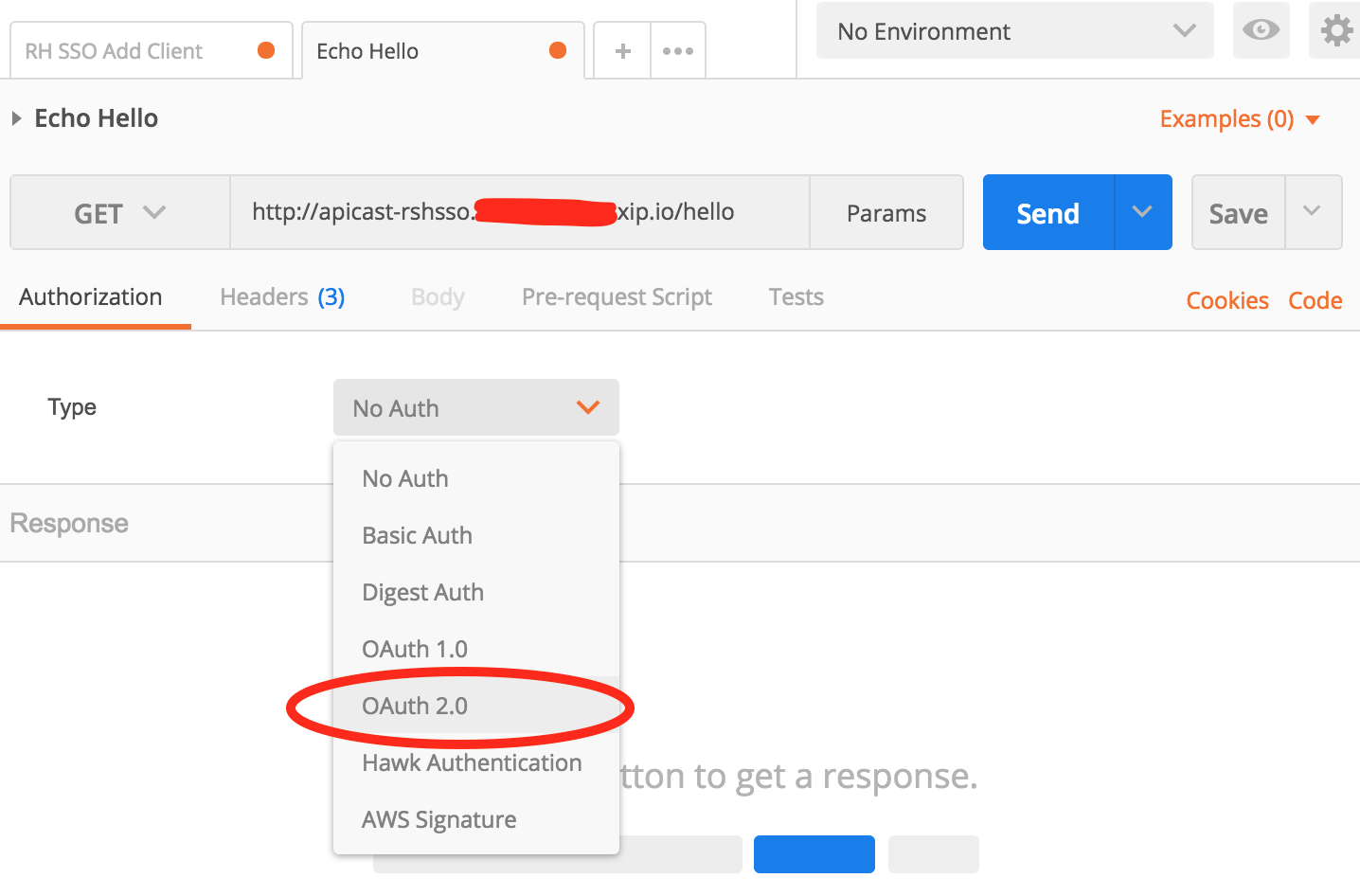
For GATEWAY, choose APICast Self Managed. For AUTHENTICATION choose Oauth 2.0. Then click Update Service
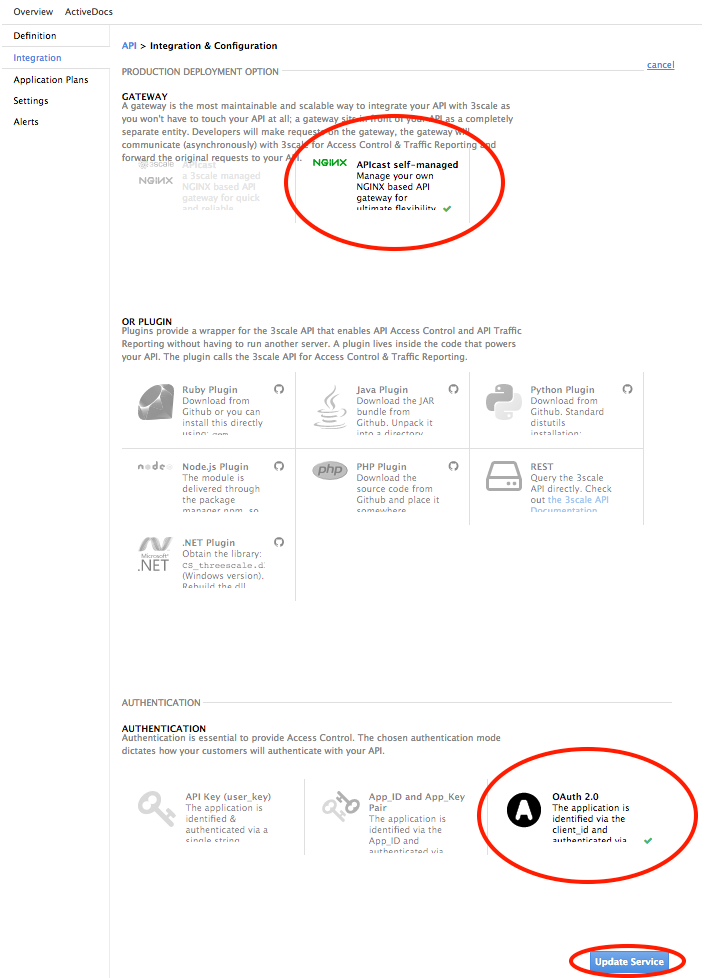
Click add the base URL of your API and save the Configuration
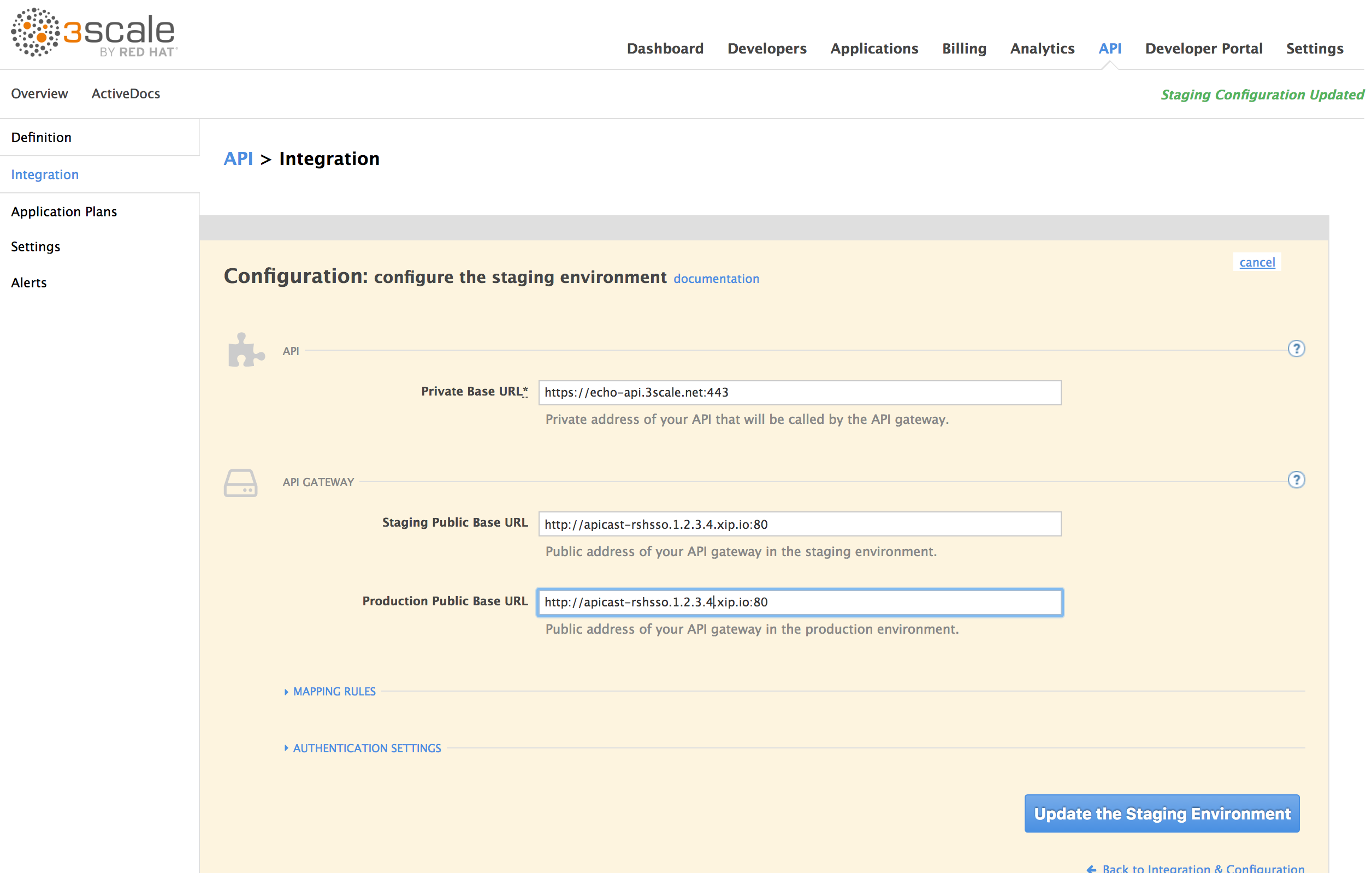
Keep Private Base URL as it is (or enter your desired API Back end URL).
Set your Staging Public Base URL and Production Public Base URL both to be http:// apicast-rshsso.rhel-box-ip.xip.io
Click Update the Staging Envirnonment
 Set your credentials location to Headers:
Set your credentials location to Headers:
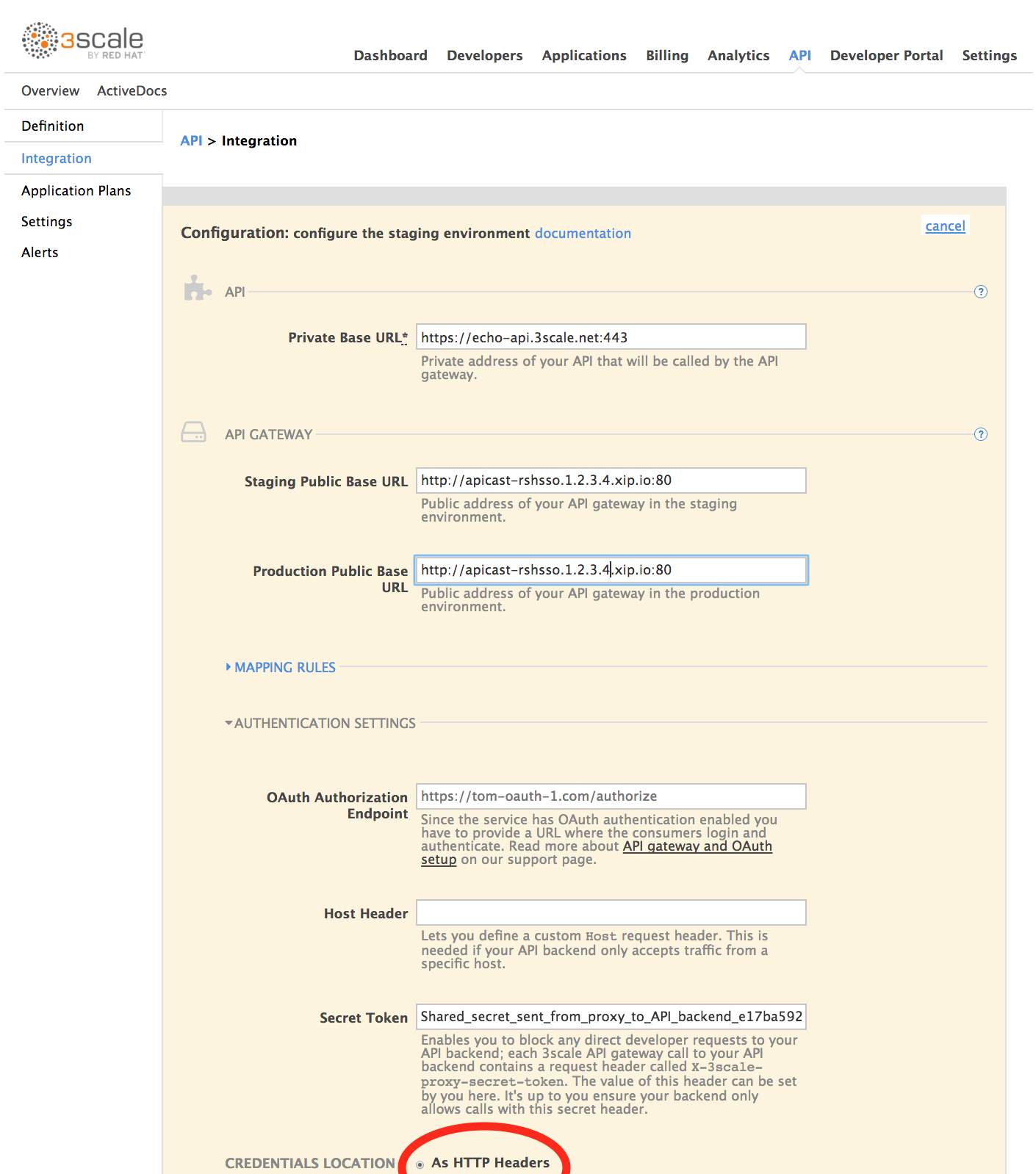
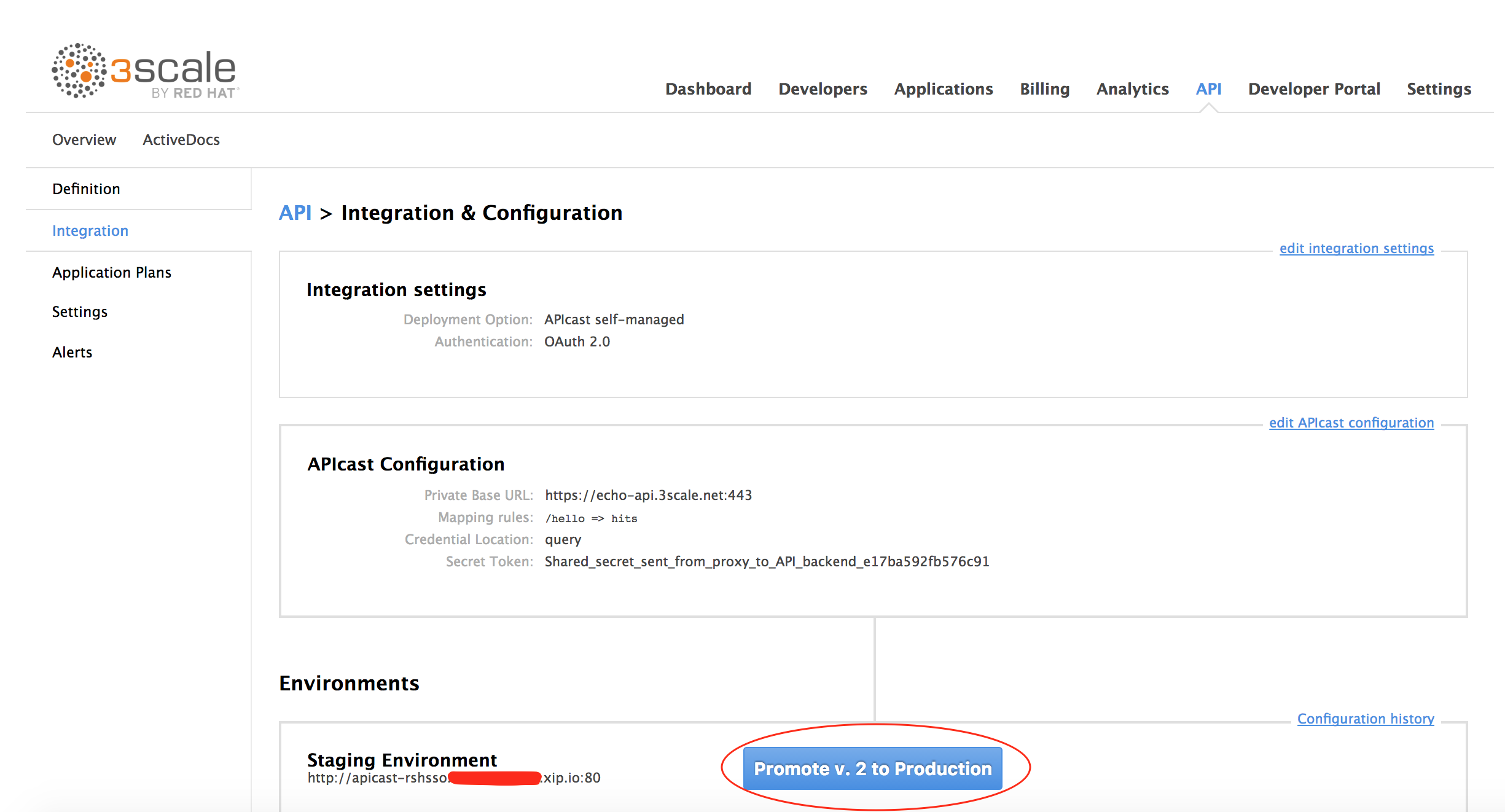
Go to API -> Integration. Click Promote v.x to Production
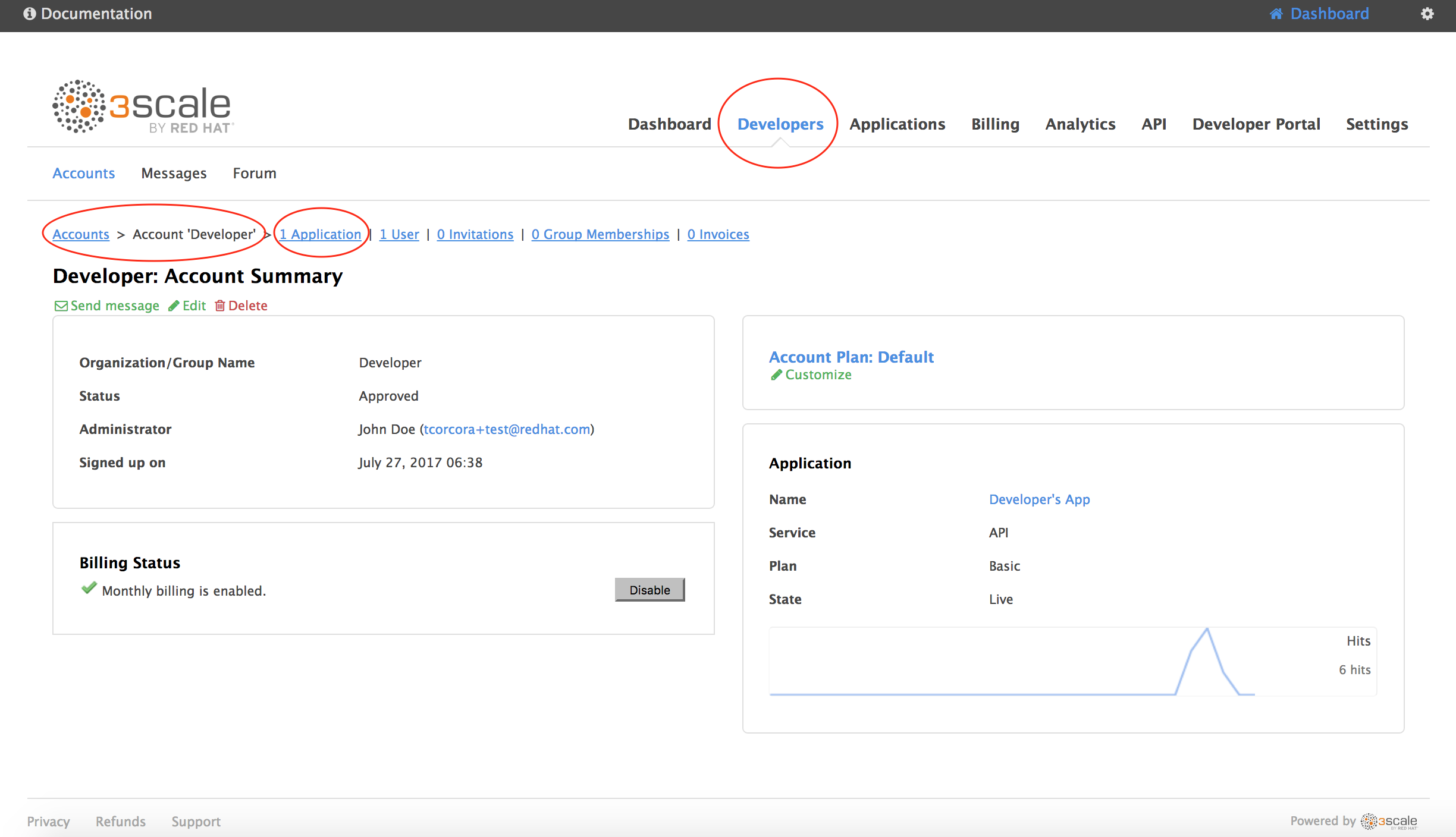
Choose Developers - Account Developer - 1 Application
Open your only Application (or choose one in your Oauth API if you have more)
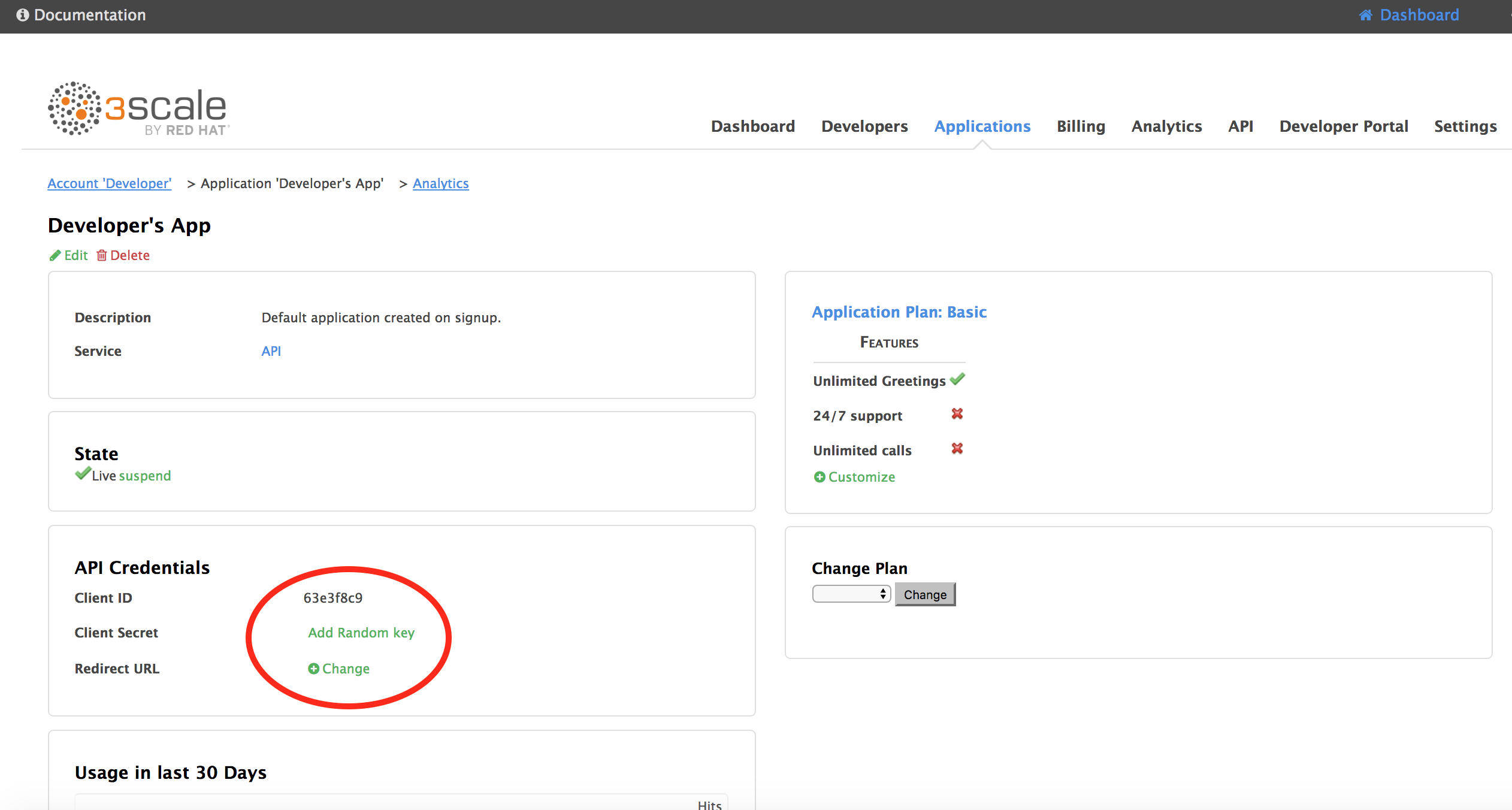 Add Random Key
Add Random Key
Set your Redirect URL to be https://www.getpostman.com/oauth2/callback
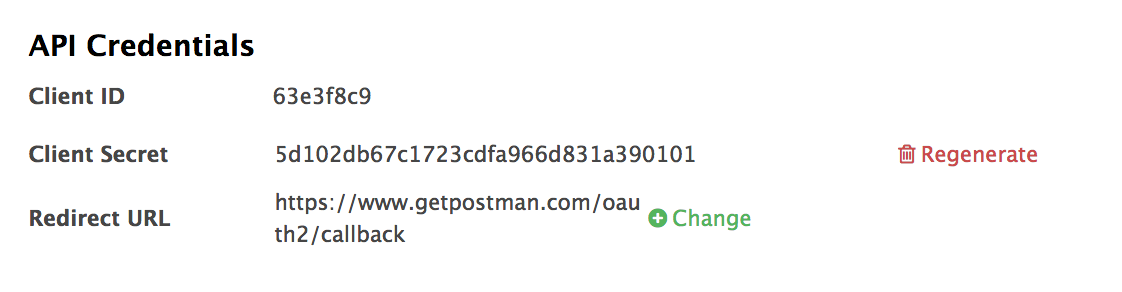 Copy your API Credentials for later. Refered to as
Copy your API Credentials for later. Refered to as
client-id
client-secret
redirect-url
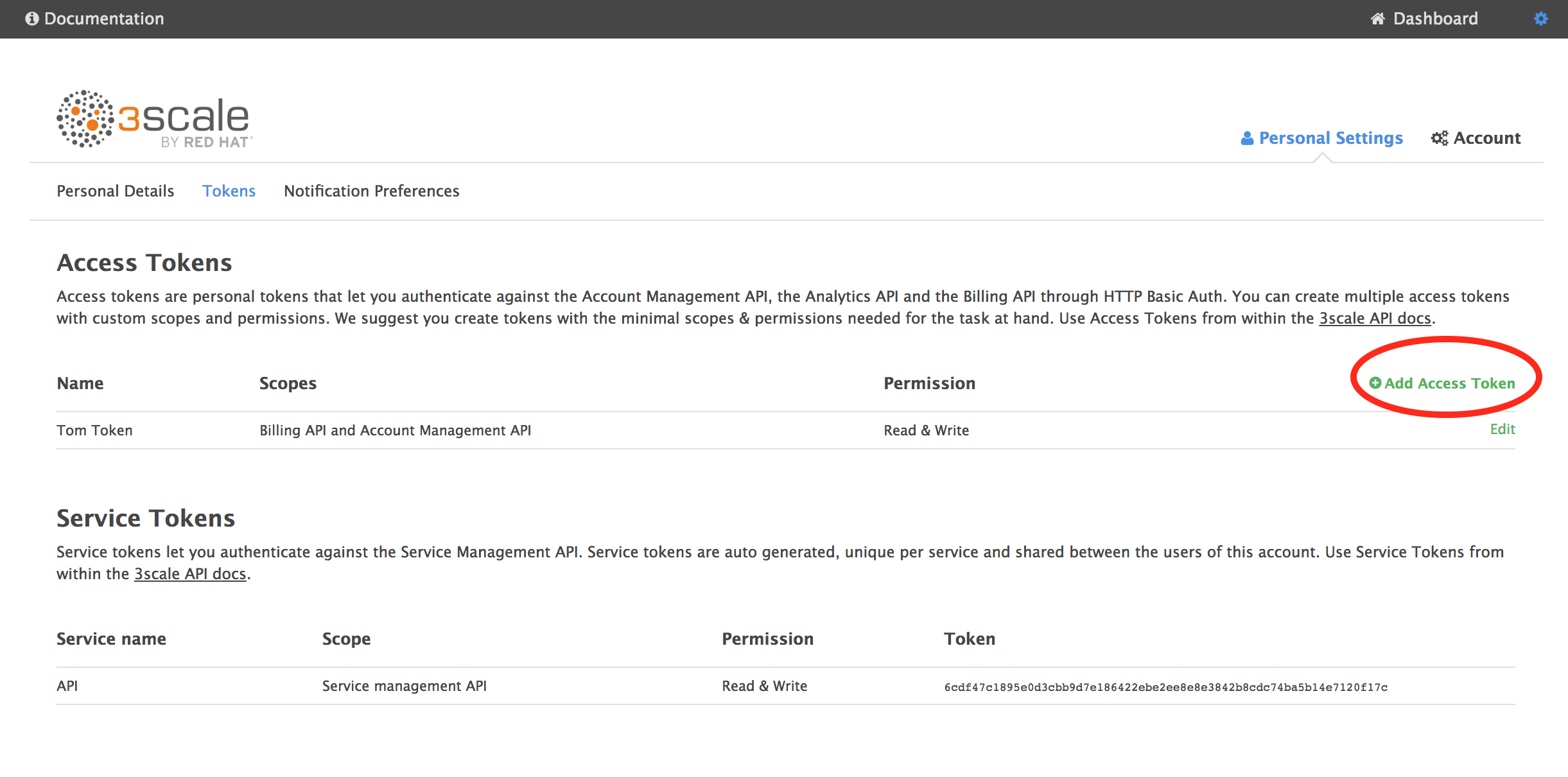
Next, get your 3scale Access token (used to create gateway). Go to Gear sign - Personal Settings - Tokens
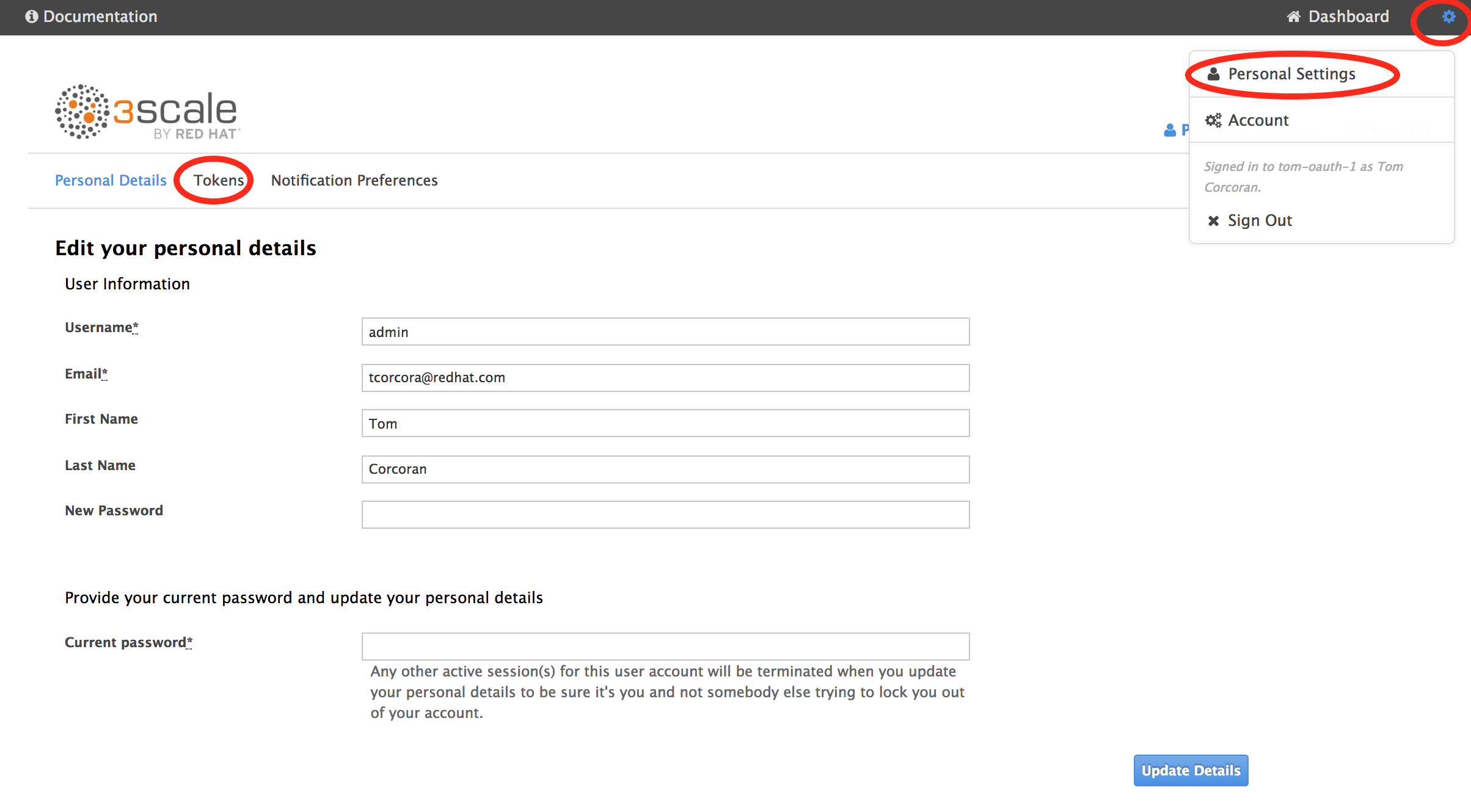
Name it, give it read/write access to all scopes and Create Access token. Copy it (you won't be able to see it again).
We'll refer to this your 3scale-access-token
Login to Master
Create a Realm for 3scale Oauth. Name it. We'll refer to it as 3scale-oauth-realm
Test your realm hitting it in a browser
http:// sso-rhsso.rhel-box-ip.xip.io/auth/realms/3scale-oauth-realm (replacing 3scale-oauth-realm with your realm name)
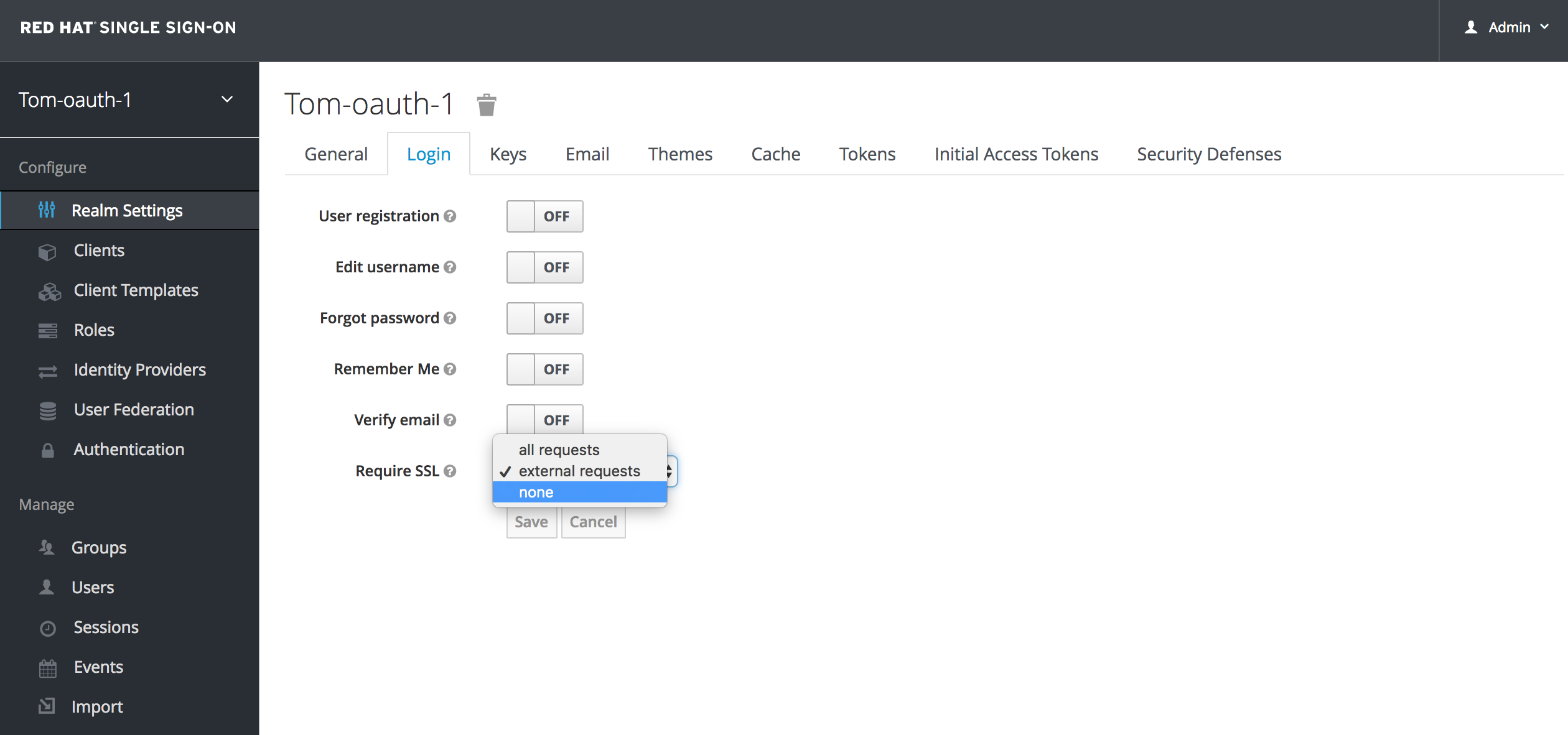
Relax SSL only requirement (for a POC, never in production). As shown under the Login Tab - set it to none and Save.
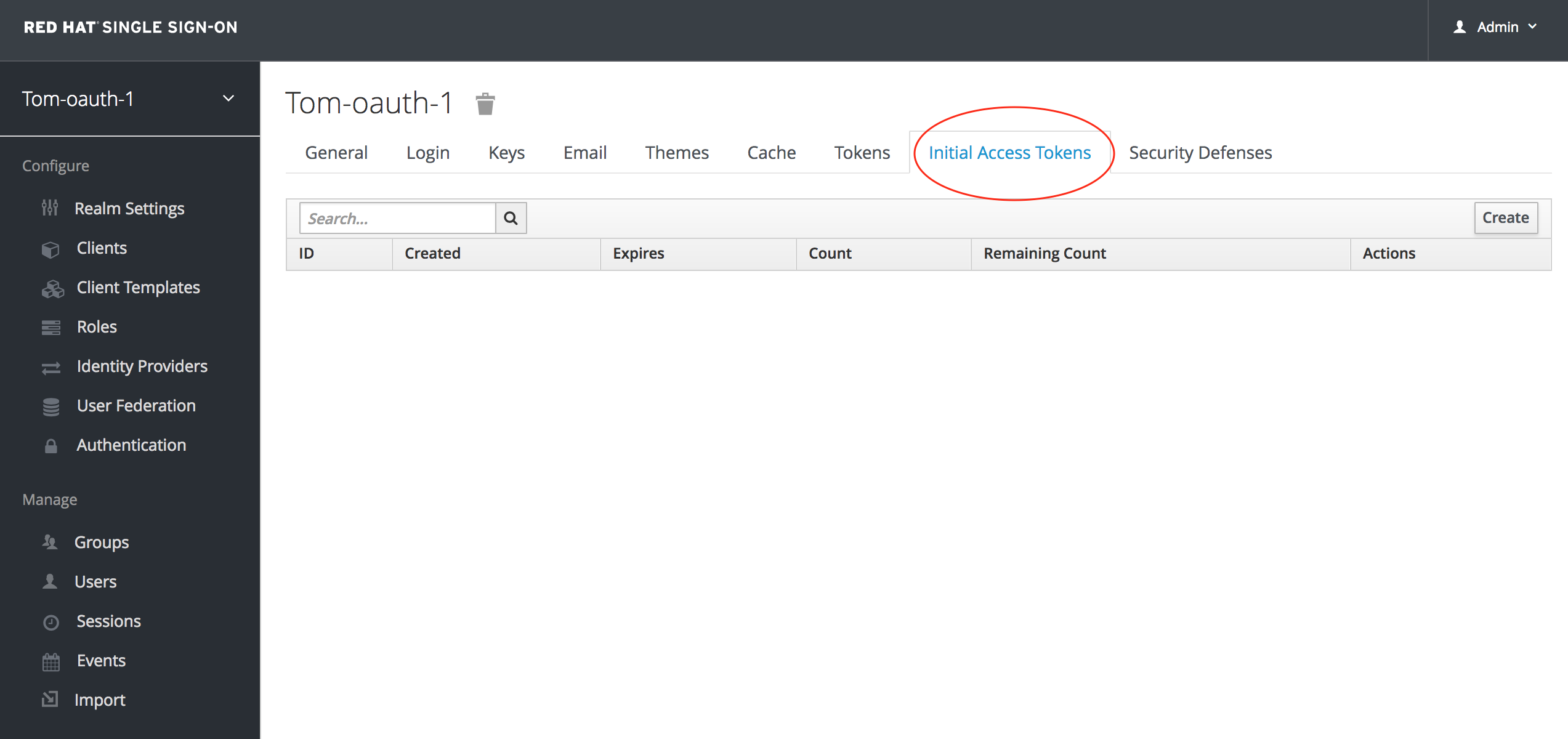
Choose Initial Access Token (this is a token we will use for a Red Hat SSO API call shortly)
Set your expiration and count to be non zero values.
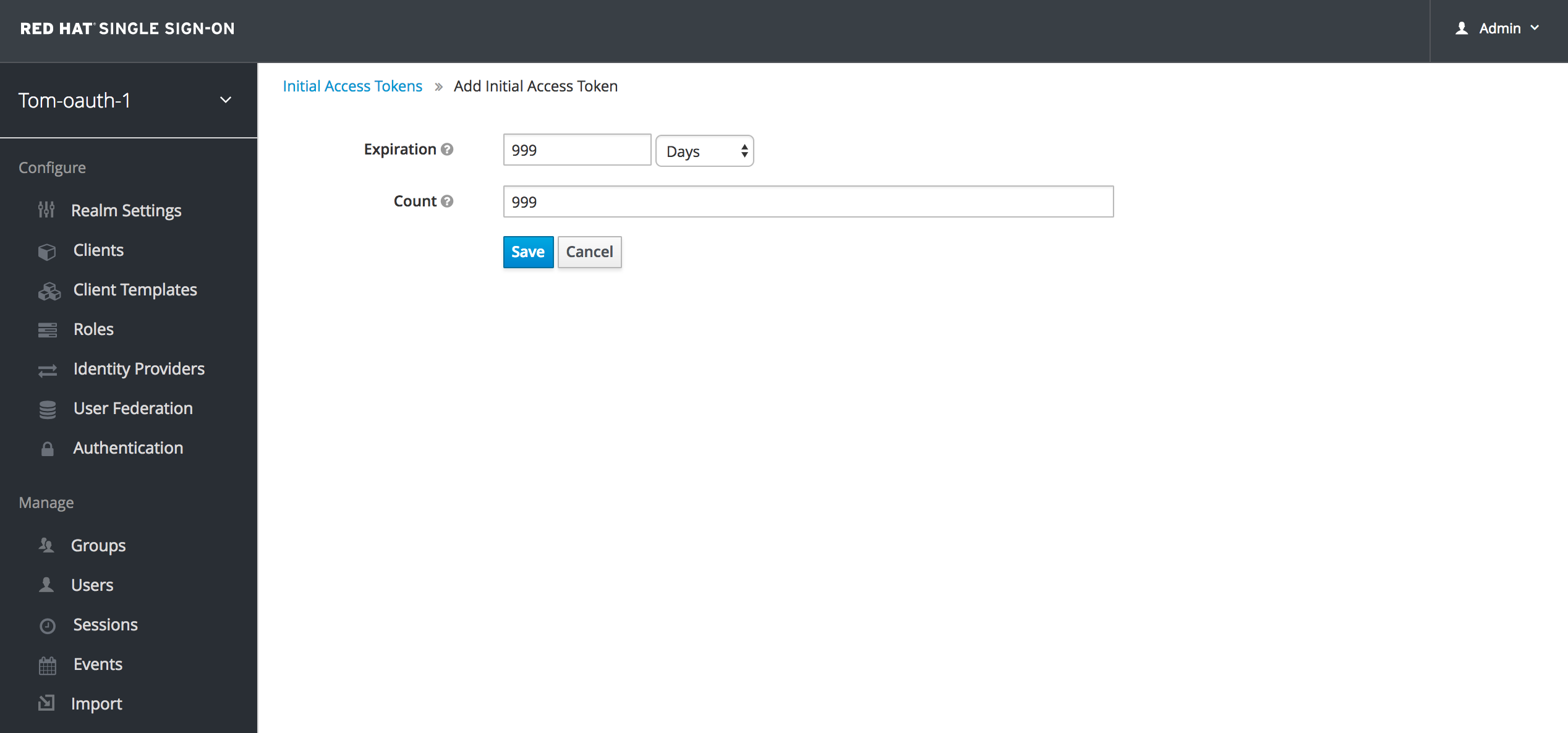
Save it. Your Initial Access Token will appear. Copy it, you won't be able to retrieve it again. We'll refer to it as your initial-access-token
Create a user on RH SSO. For simplicity I'll refer to as rh-sso-user-id.
Enter your equivalents to the following and Save:
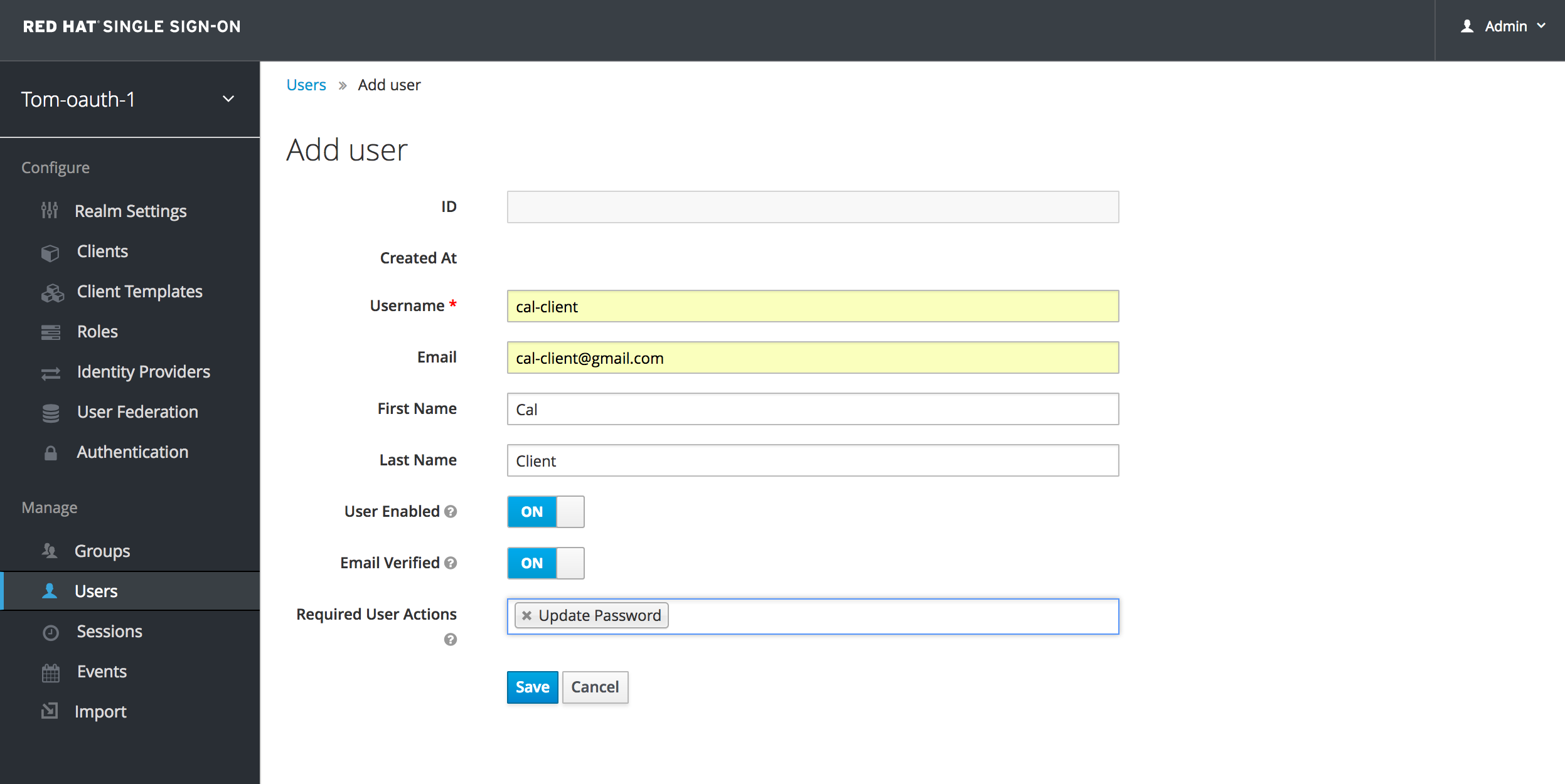
On the Credentials tab, add New Password and Password Confirmation and reset. I'll refer to it as rh-sso-user-password
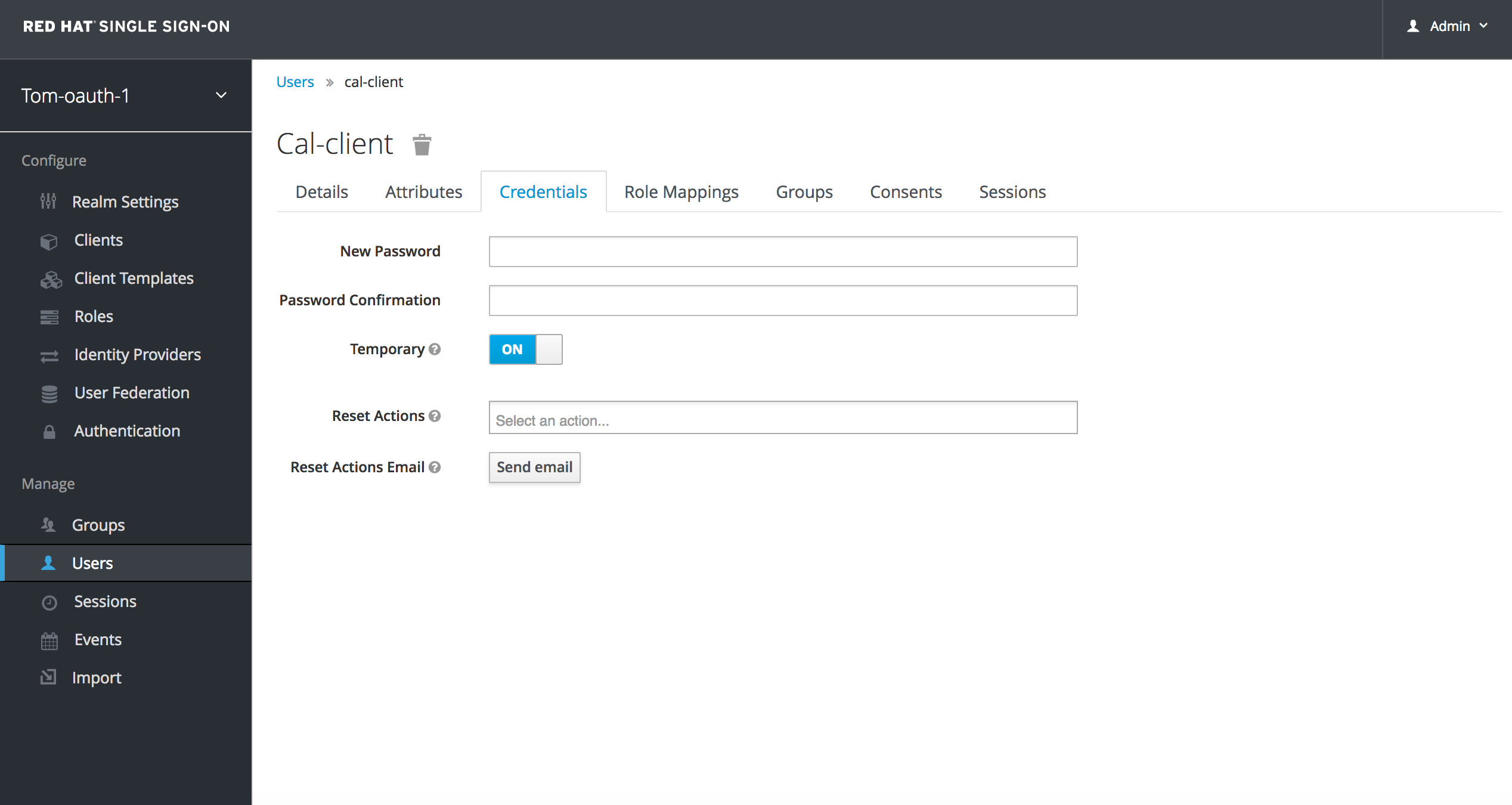
In Postman, import the postman JSON RHSSO_3scaleGist.postman_collection.json in this repo.
Open RH SSO Add Client request add client to Red Hat SSO (Client credentials on RHSSO need to be the same as Application Credentials set on 3scale above)
Set the realm name in the address (to reflect rhel-box-ip) and the Bearer token to your initial-access-token retrieved above.
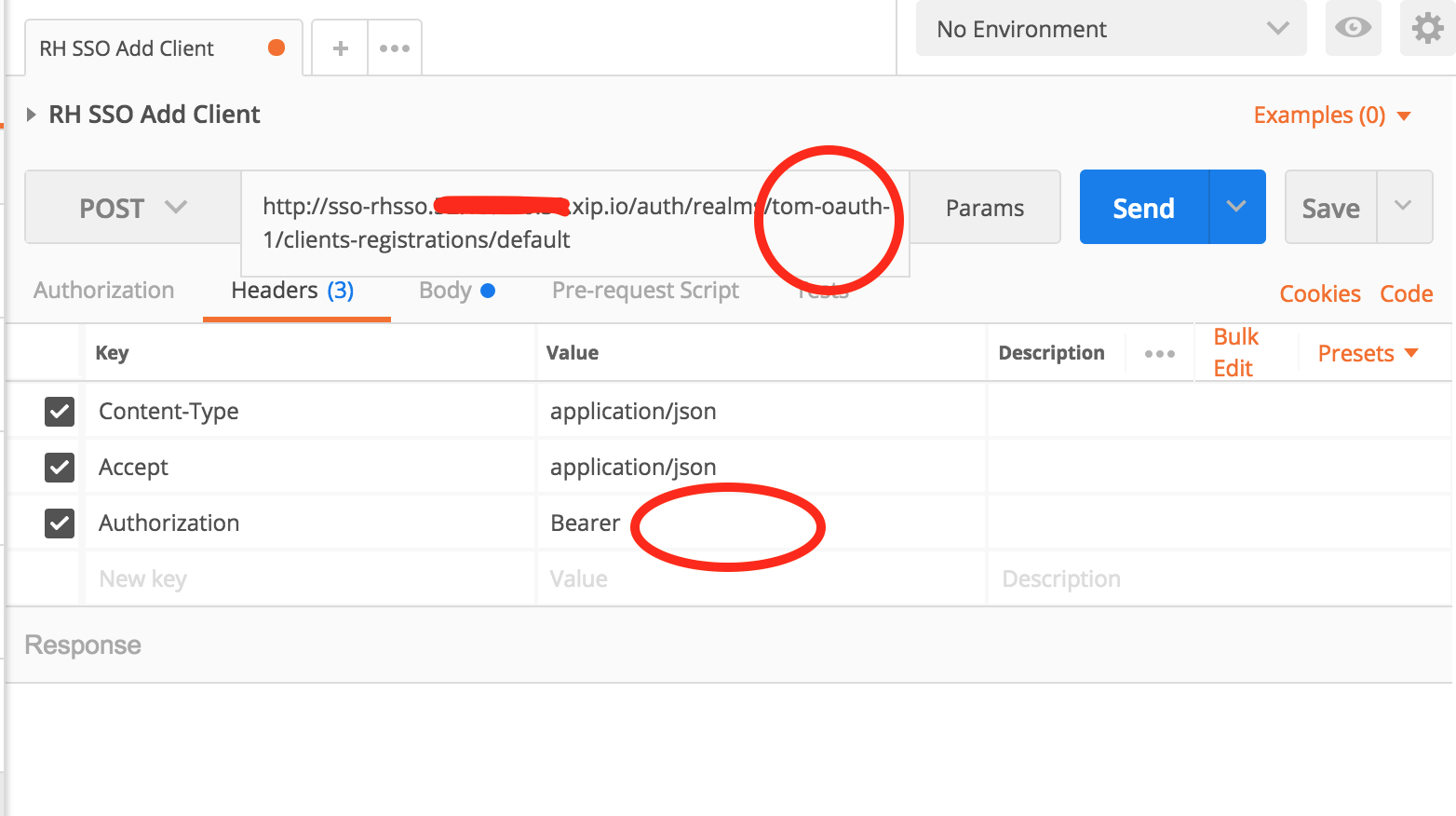 Save it.
Switch to the Body tab. Enter the client-id, client-secret and redirect-url you set in 3scale above (Redirect URL is called redirectUris here)
Save it.
Switch to the Body tab. Enter the client-id, client-secret and redirect-url you set in 3scale above (Redirect URL is called redirectUris here)
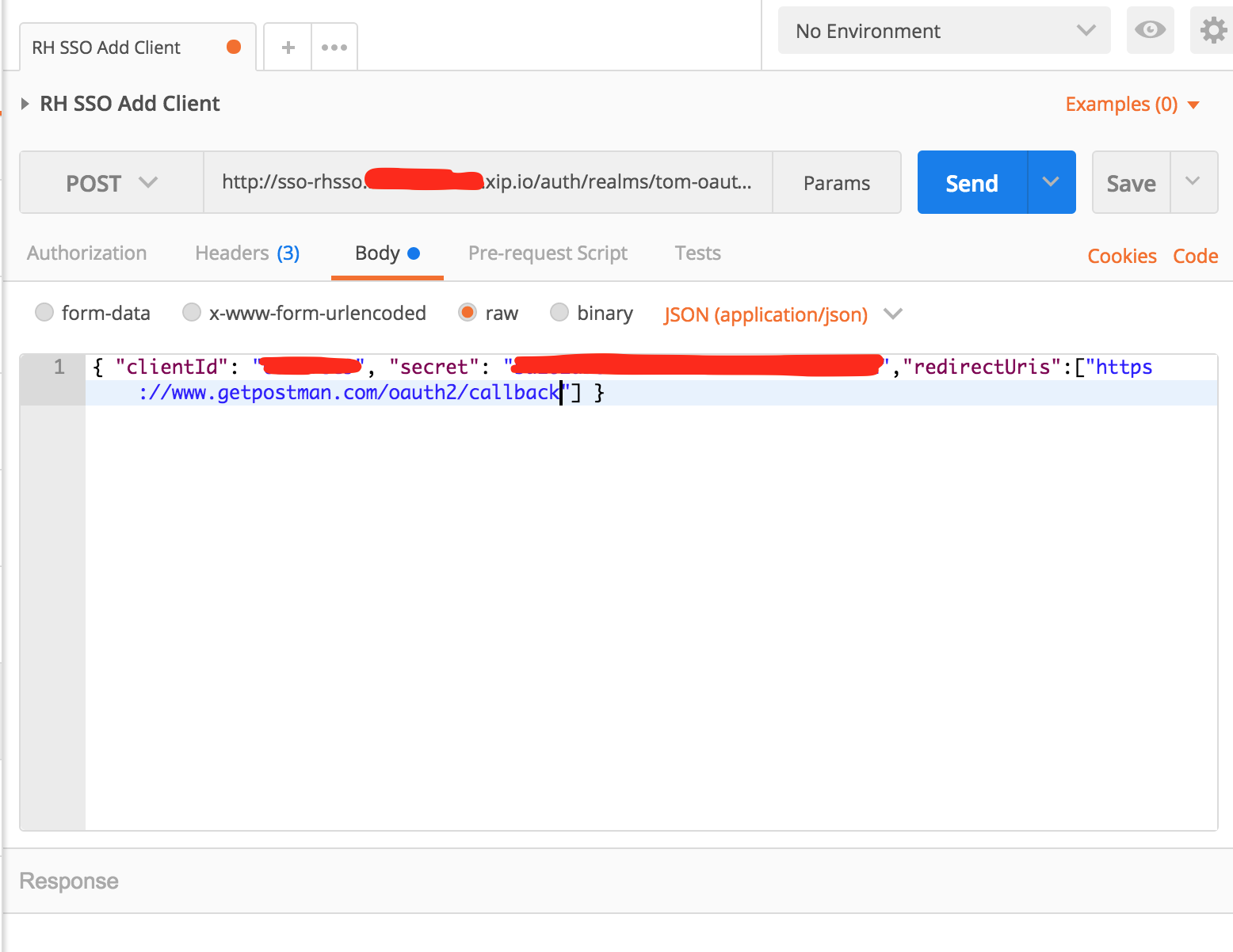
Save and Send it. You should get back some JSON and 201 created HTTP status.
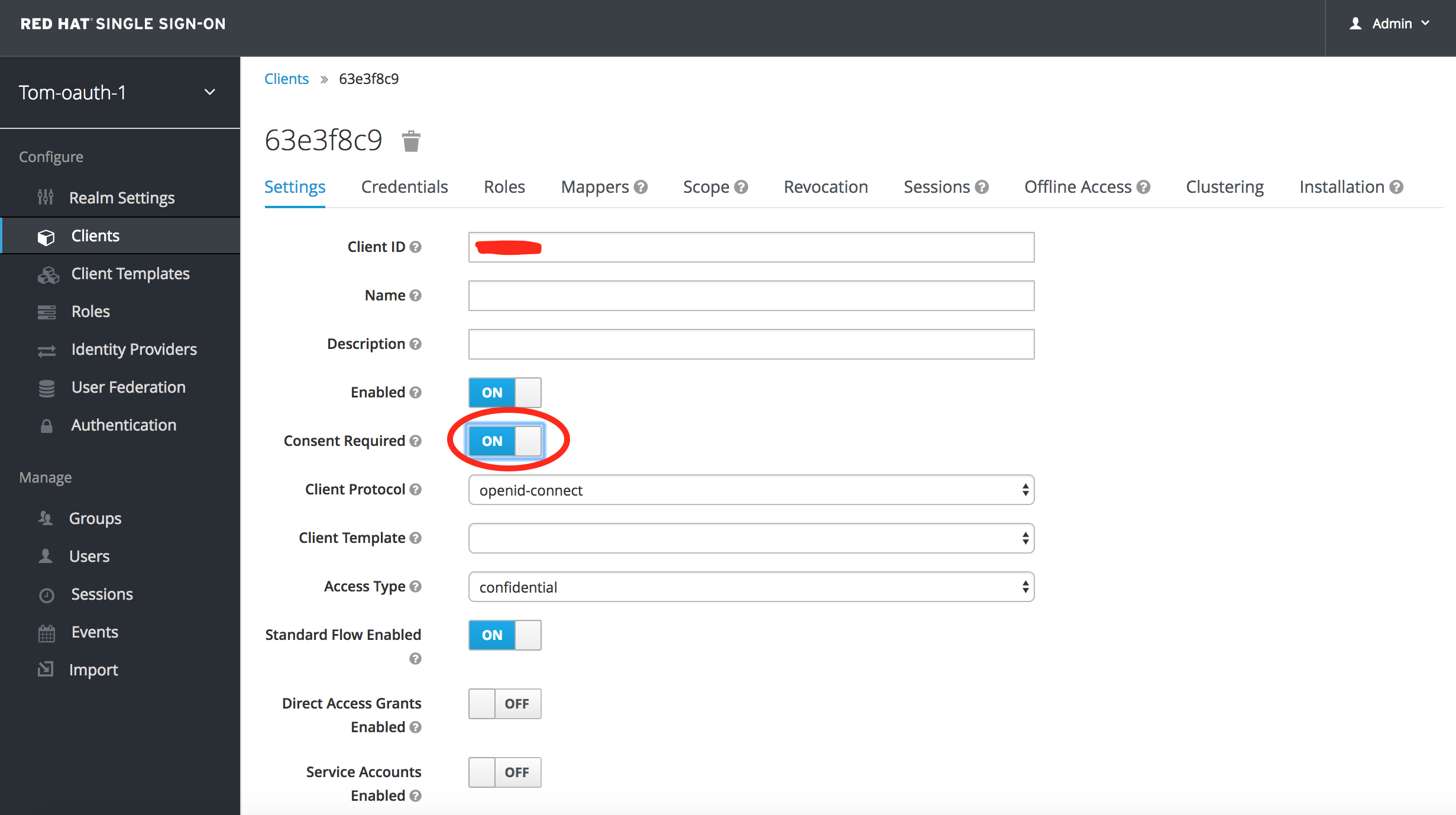
In Red Hat SSO, click on the Clients view on the Left hand side. Select your new client (client-id)
Assuming you want to give the user ability to grant access to the Application to access their data (we do), click Consent Required. Save
Login to Openshift and make the following commands
oc login
(default credentials are developer/developer)
Create your project, e.g. with something like these values:
oc new-project "3scalegateway-3scale-oauth-realm" --display-name="3scalegateway-3scale-oauth-realm" --description="3scalegateway-3scale-oauth-realm" (replacing 3scale-oauth-realm with your realm name)
oc secret new-basicauth apicast-configuration-url-secret --password=https:// 3scale-access-token @ 3scale-domain (remove whitespace, replacing 3scale-domain with the URL to your SaaS on On Prem 3scale API Manager)
oc new-app -f https://raw.githubusercontent.com/3scale/3scale-amp-openshift-templates/2.0.0.GA-redhat-2/apicast-gateway/apicast.yml
Your gateway will deploy in a couple of minutes.
TIP Scale it down to 1 Pod - that way if you want to look up logs, they can only be in the remaining Pod.
Open web Console https:// openshift-host :8443 and open 3scalegateway-3scale-oauth-realm (replacing 3scale-oauth-realm with your realm name)
Go to Applications -> Deployments -> apicast -> Environment
Add this ENV variable: RHSSO_ENDPOINT and set it to: http:// sso-rhsso.rhel-box-ip.xip.io/auth/realms/3scale-oauth-realm (replacing 3scale-oauth-realm with your realm name)
Save
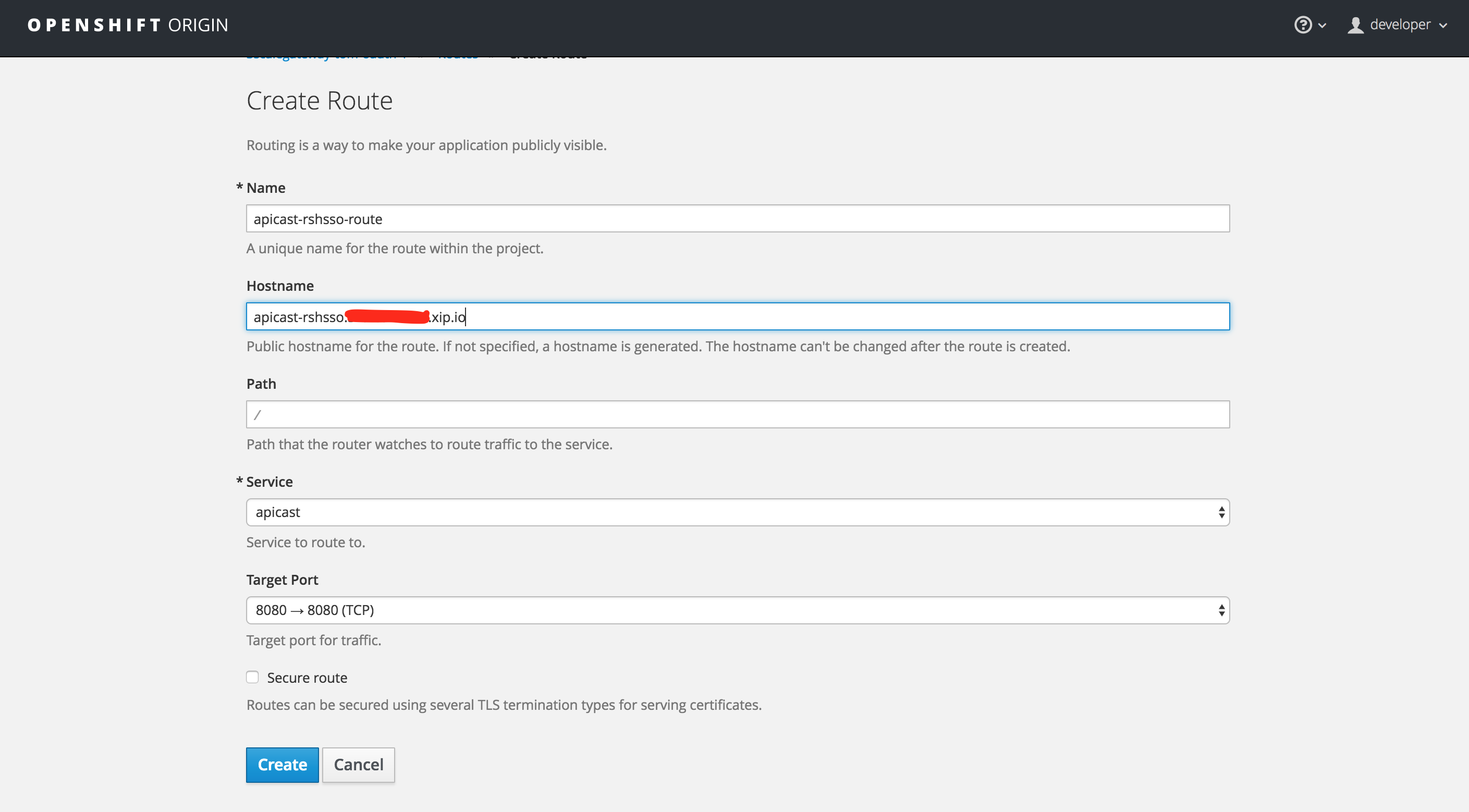
On Openshift web Console -> Overview -> Create Route.
Name: apicast-rshsso-route
Hostname: apicast-rshsso.rhel-box-ip.xip.io
Leave the rest of the defaults and click Create
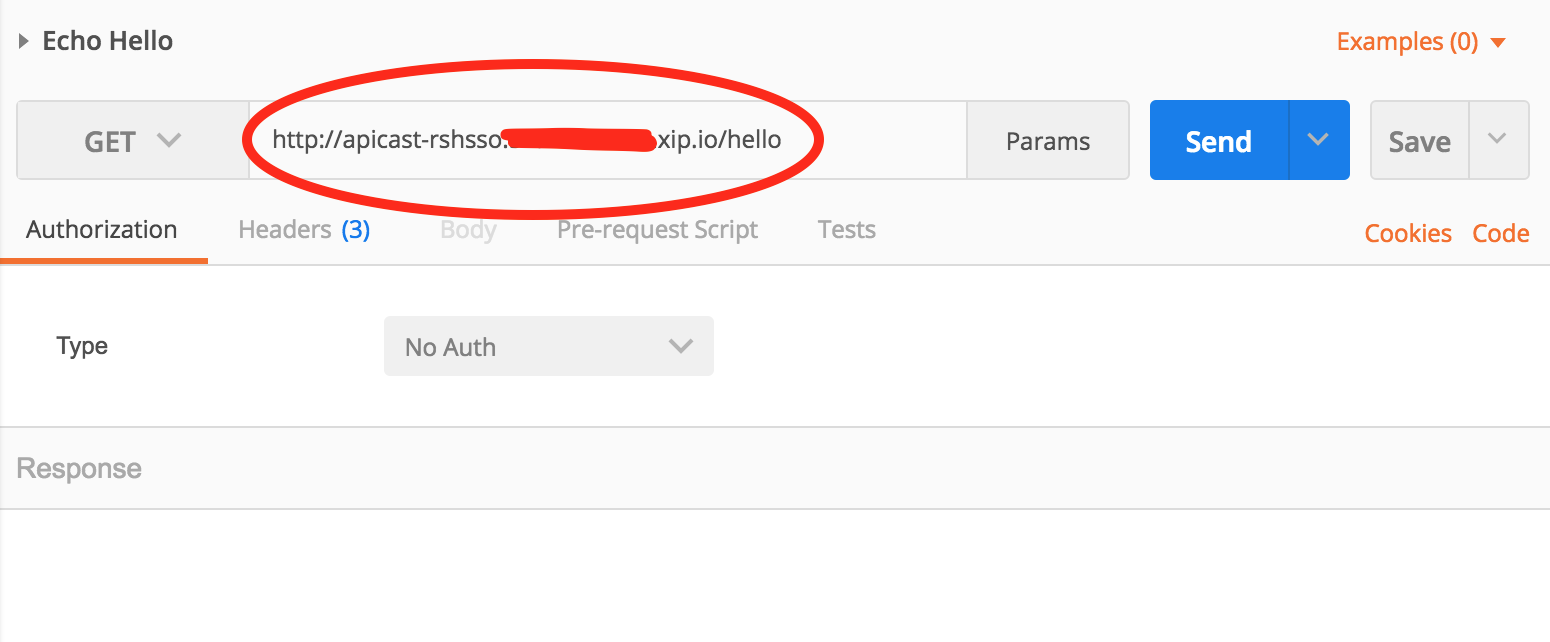
Open Echo Hello. Set your GET URL to be http:// apicast-rshsso.rhel-box-ip.xip.io/hello
Set these parameters and
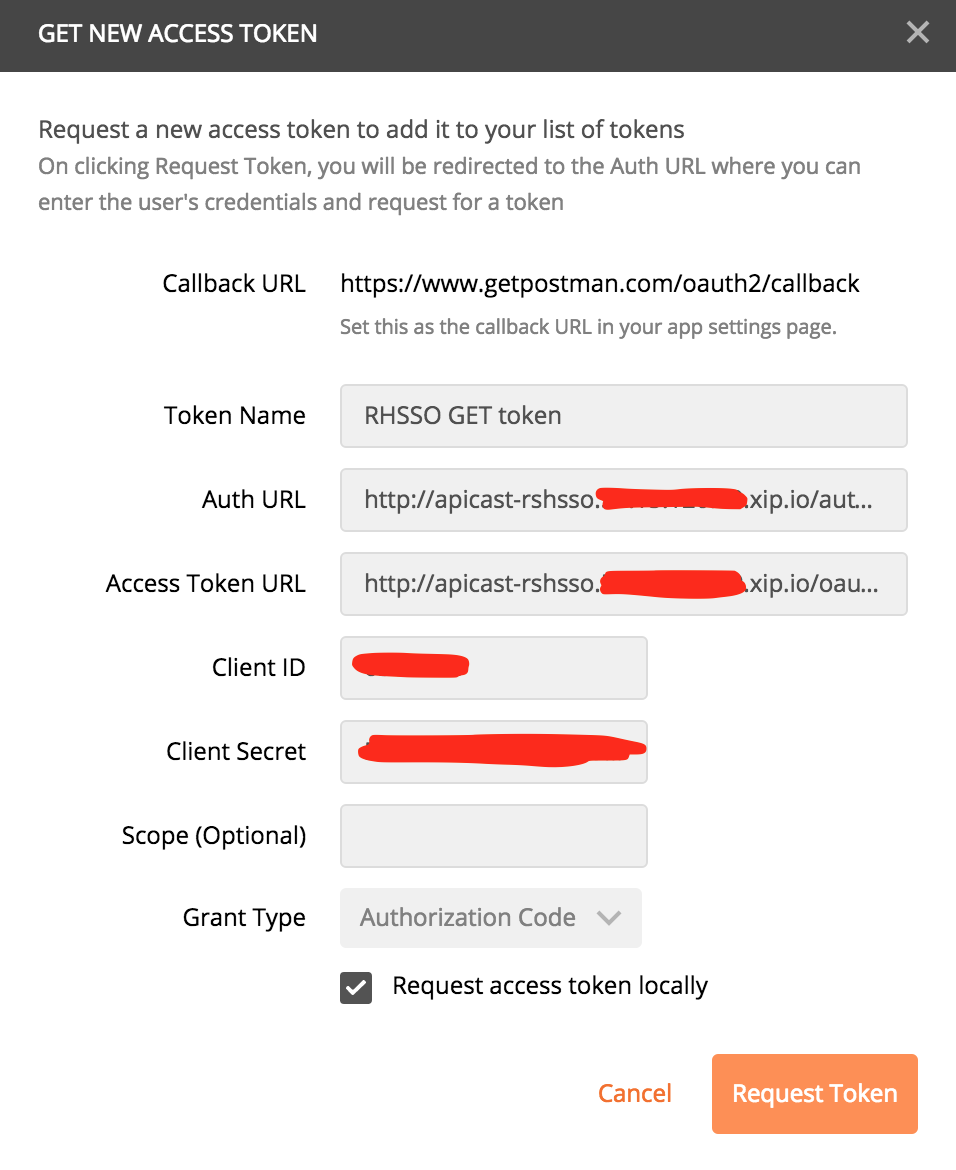
Click Get New Access Token orange button
Auth URL: http:// apicast-rshsso.rhel-box-ip.xip.io/authorize
Access Token URL: http:// apicast-rshsso.rhel-box-ip.xip.io/oauth/token
Client ID client-id
Client Secret client-secret
Login as the user you created in RH SSO (rh-sso-user-id/rh-sso-user-password). (styling is always missing so ignore for now)
After authentication, you'll be prompted to create a new Password. Do this.
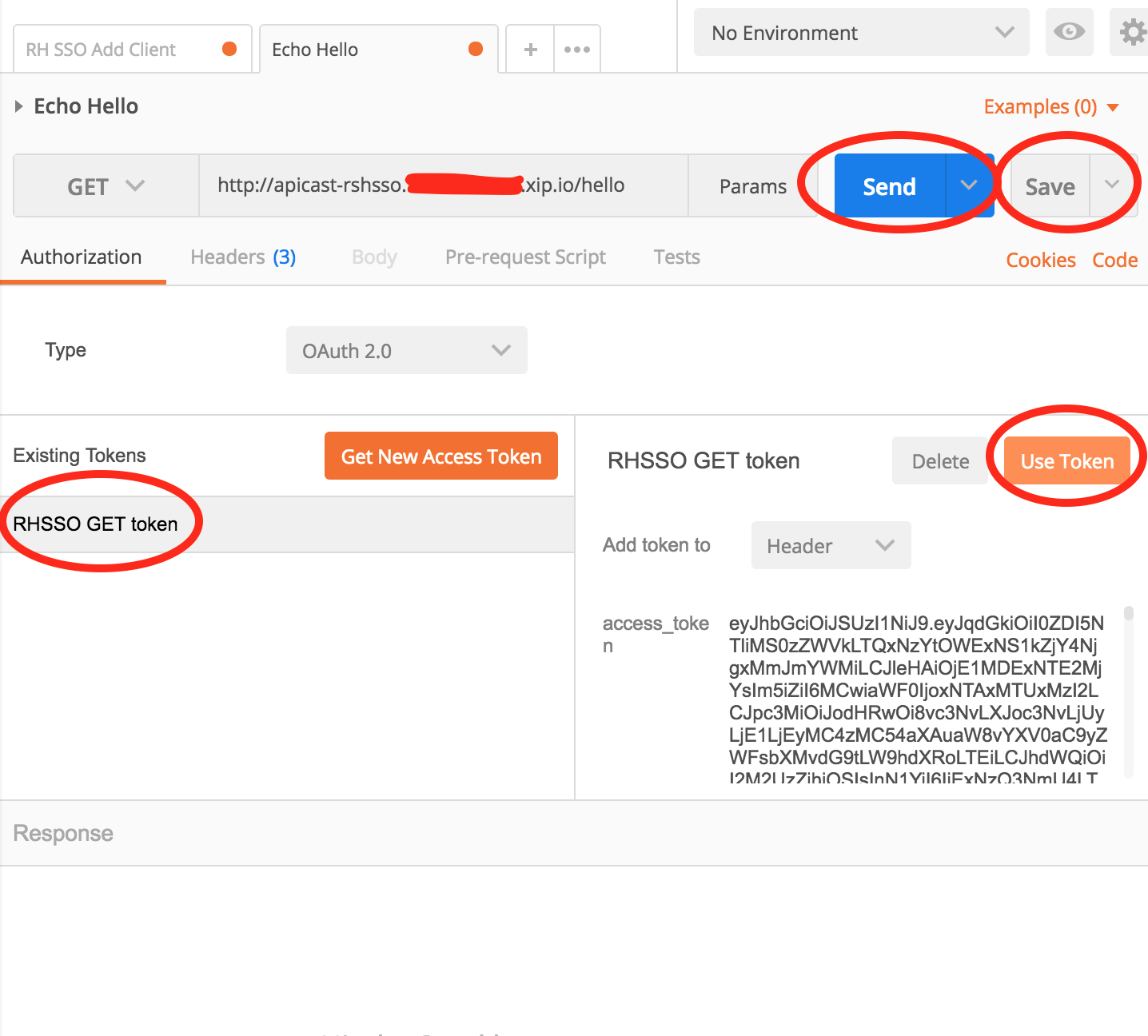
A Token (RHSSO Get Token) will be returned to Postman. Click it then click Use Token.
Click Save then click Send. You should get a successful API Response.
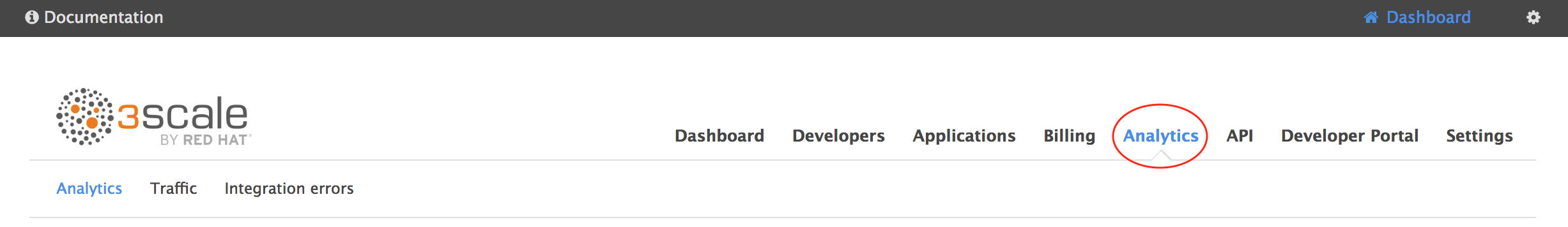
Go to your 3scale Analytics. Your counts should increment with each call.
Return to postman and insert a random characted into the JWT and Use Token and repeat. Authorization should fail.
7 - Test your JWT on https://jwt.io (optional)
Go to https://jwt.io
Paste into the Encoded box on the left the JWT that got inserted into the Bearer token Authorization Header after you selected Use Token.
On the right, you'll see some decoded payload data representing the user and client.
Go to Red Hat SSO -> Realm Settings -> Keys
Copy the Public Key
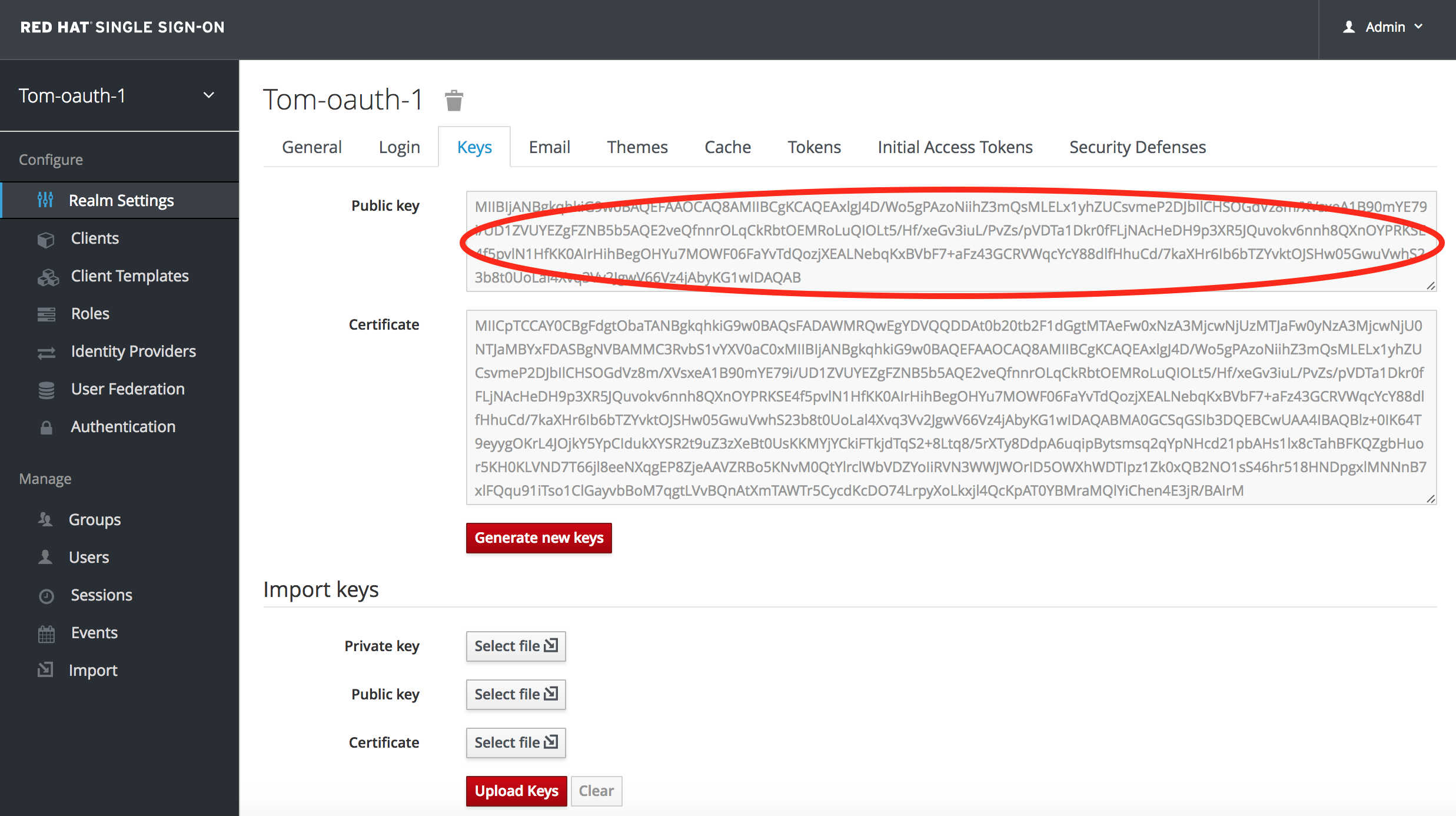 Insert Public Key as follows:
Insert Public Key as follows:
-----BEGIN PUBLIC KEY-----
public key goes here
-----END PUBLIC KEY-----
Back in jwt.io, paste this into the Public Key or Certificate box on the right and the red Invalid Signature banner should turn to a blue Signature verified one. Alter either the payload or the public key and signature validation will fail. This simulates the signature validation that hapeens on the gateway.
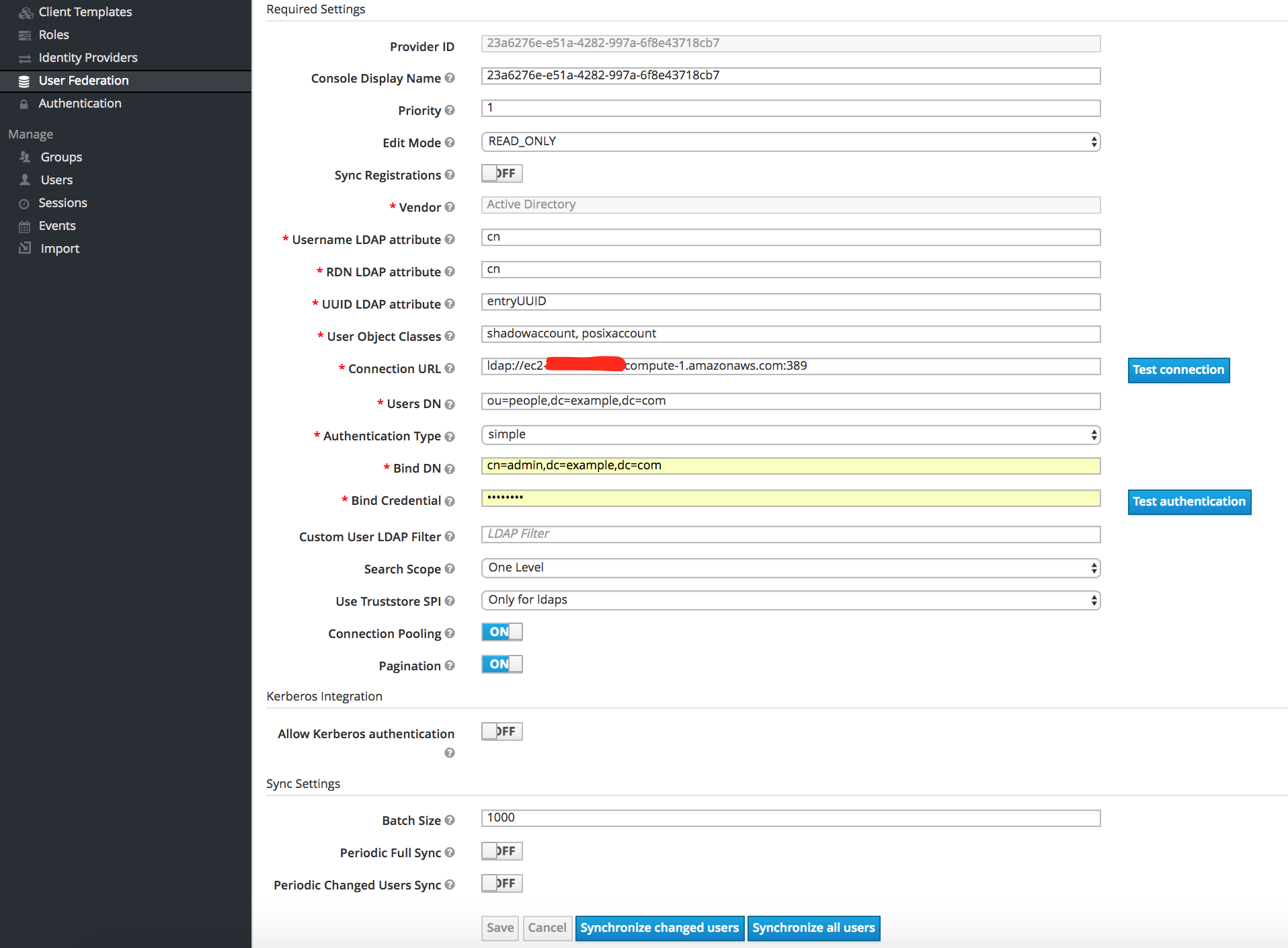
Go to: User Federation -> Add Provider -> ldap
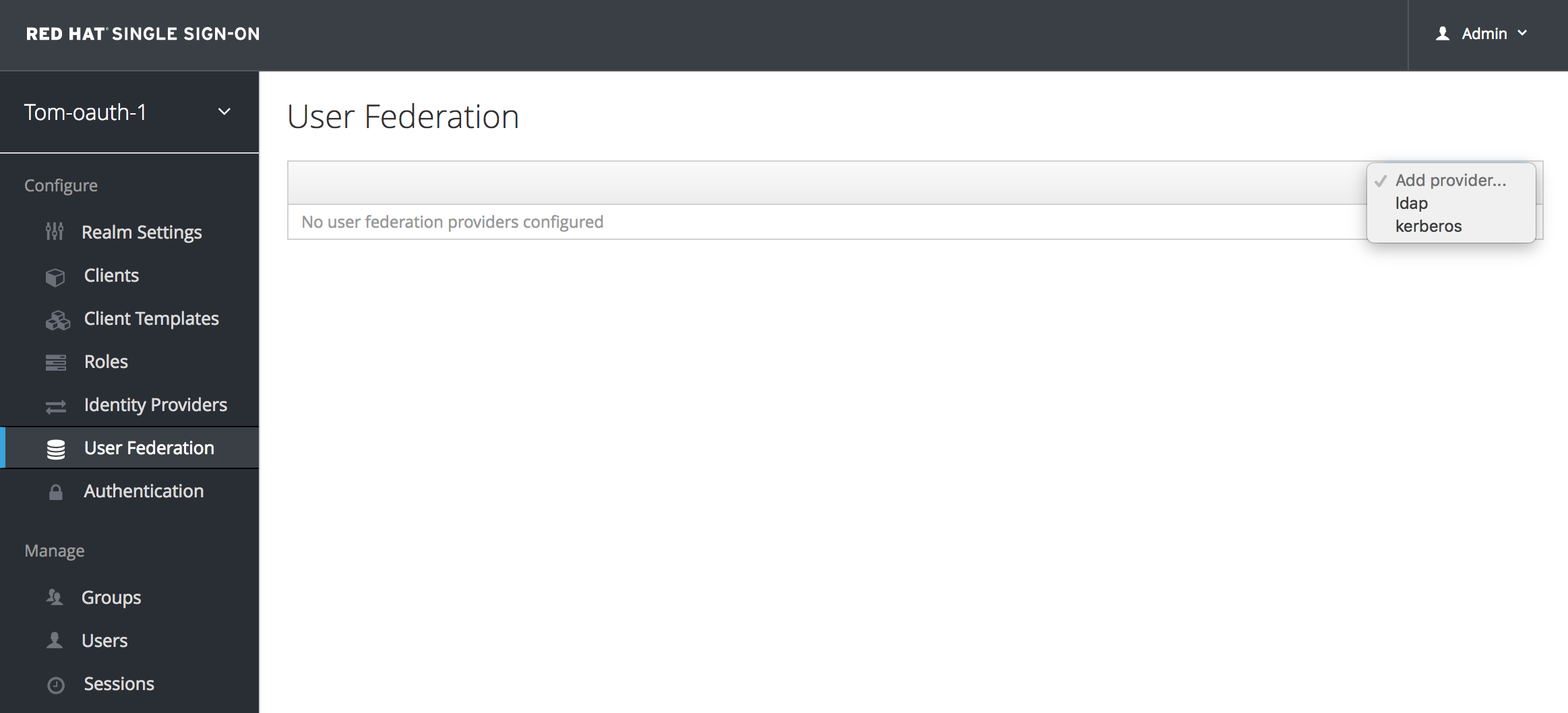
Enter the following (or your equivalents), testing connection and authentication as you go then Save:
Console Display Name: open-ldap
Priority 1
Edit Mode Read Only
Vendor Active Directory
UUID LDAP attribute entryUUID
User Object Classes shadowaccount, posixaccount
Connection URL ldap://ldap-url:389
***test it
Users DN ou=people,dc=example,dc=com
Authentication Type Simple
Bind DN cn=admin,dc=example,dc=com
Bind Credential ldap-password
Retest OAuth flow and API with token In Postman - this time using credentials stored on LDAP
9 - SSO into Dev Portal (based on https://support.3scale.net/docs/developer-portal/authentication#rhsso)
In 3scale, go to Settings -> Developer Portal -> SSO Integrations.
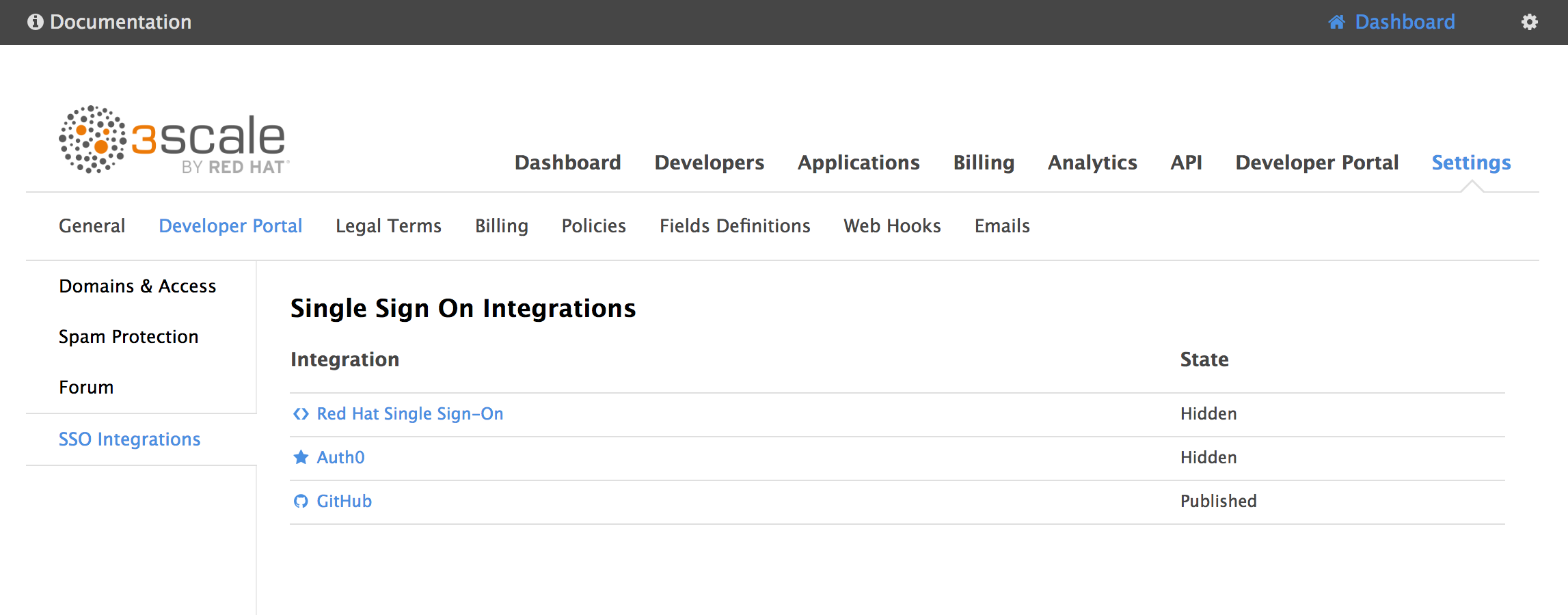
Click on Red Hat Single Sign On. Enter the following (or your desired values)
Client: 3scale-dev-portal-client
Client secret: 3scale-dev-portal-client-secret
Realm: http:// sso-rhsso.rhel-box-ip.xip.io/auth/realms/3scale-oauth-realm (replacing 3scale-oauth-realm with your realm name)
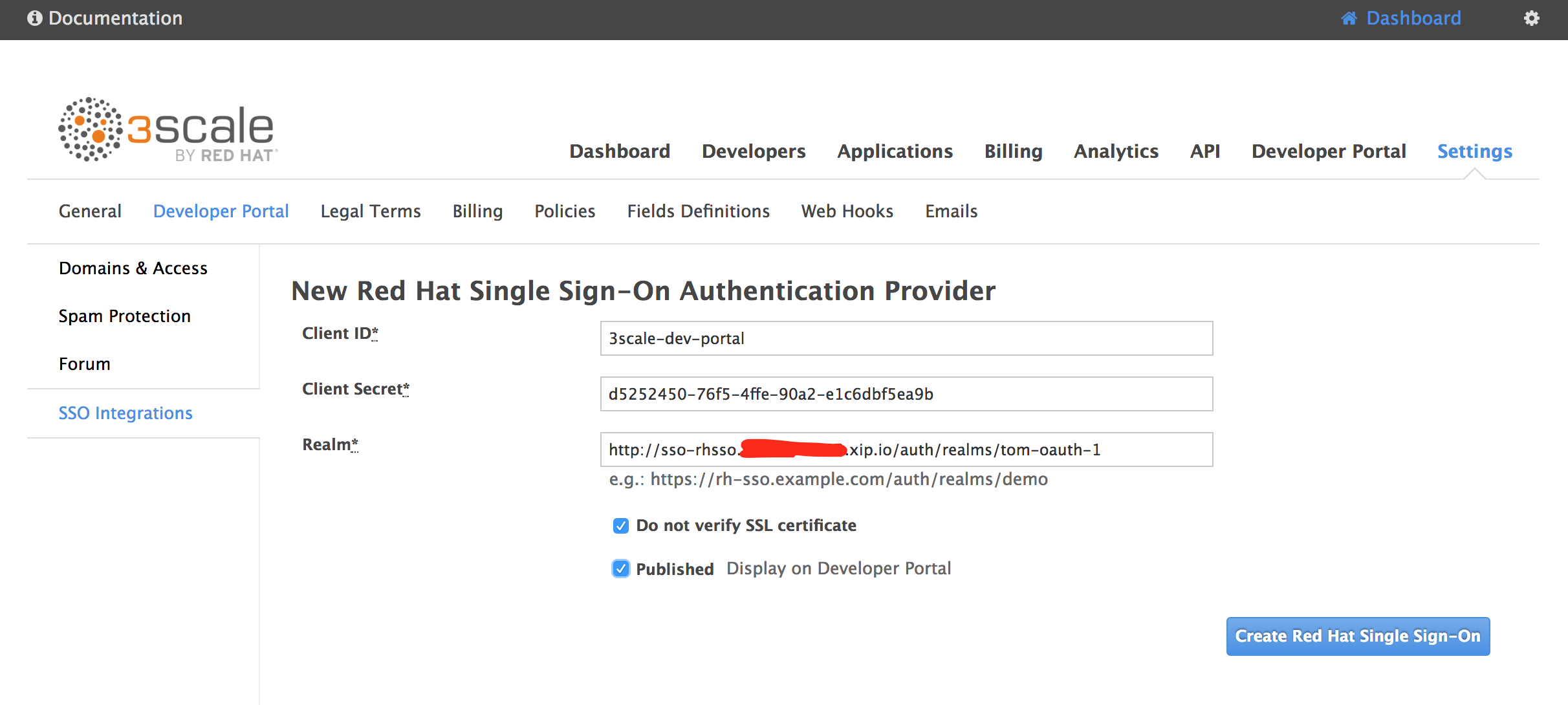
While we're in 3scale we're going to remove the secret access key for easier access (for illustration only - we would normally keep it there until our Dev Portal is ready to go live)
In 3scale go to Settings -> Developer Portal. Delete the Developer Portal Access Code and Update Account.
Next we need to add a client to your Realm in Red Hat SSO that aligns with your Dev Portal Oauth client to 3scale.
Open Postman and repeat the steps in 3 - Use Postman to create client on Red Hat Single Sign On above, replacing the data elements in the request JSON body with these (or your equivalents):
clientId: 3scale-dev-portal-client
secret: 3scale-dev-portal-client-secret
redirectUris: https:// 3scale-oauth-realm.3scale.net (replacing 3scale-oauth-realm with your realm name)
(note the redirectUris entry is the same as your 3scale admin portal url without the '-admin')
Click Send.
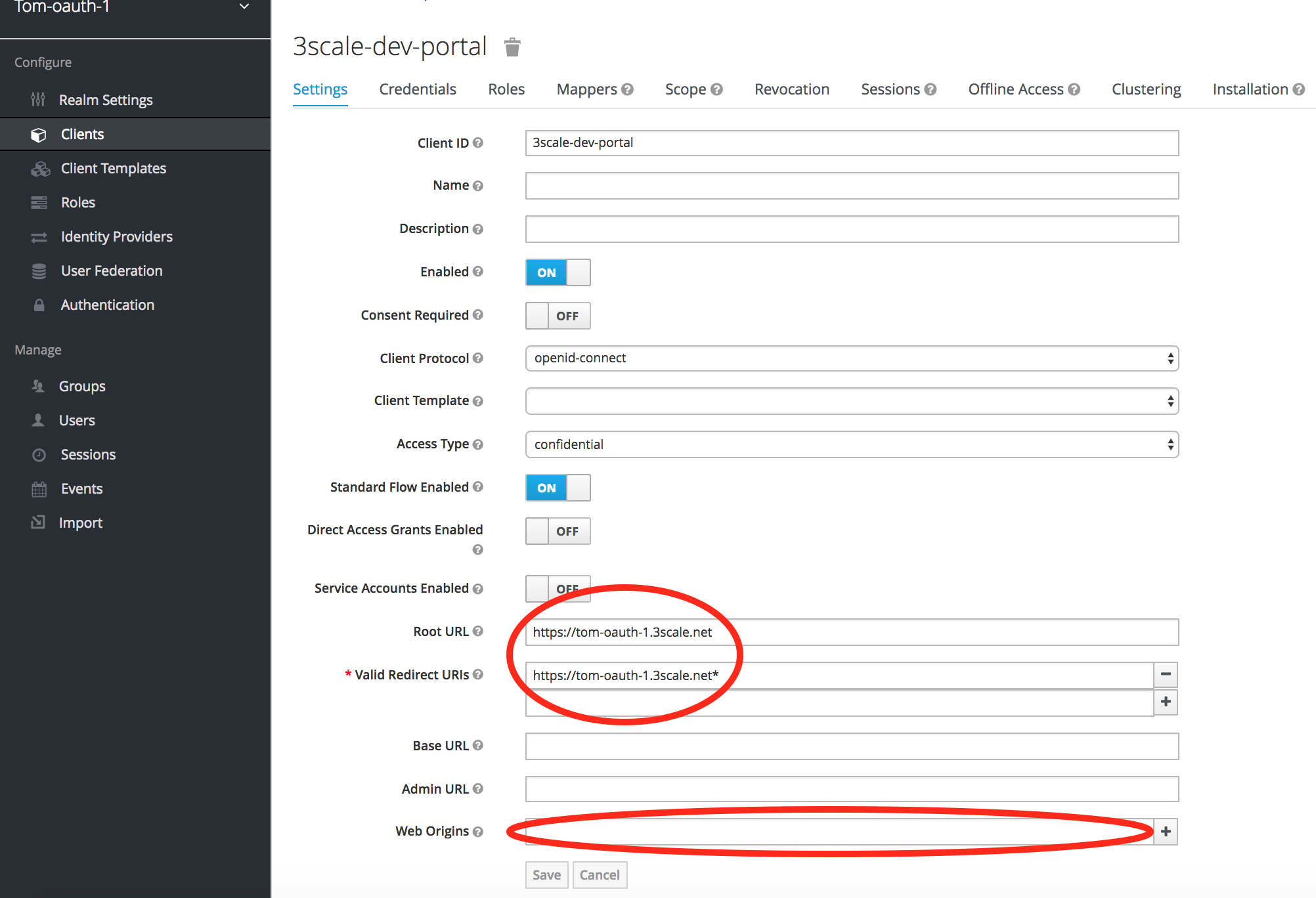
You'll need to make a couple of mods to the client generated by your Postman call.
Root URL: https://3scale-oauth-realm.3scale.net (your dev portal URL, replacing 3scale-oauth-realm with your realm name)
Valid Redirect URIs: https://3scale-oauth-realm.3scale.net* (your dev portal URL with * appended, replacing 3scale-oauth-realm with your realm name)
Web Origins: empty (delete what's there)
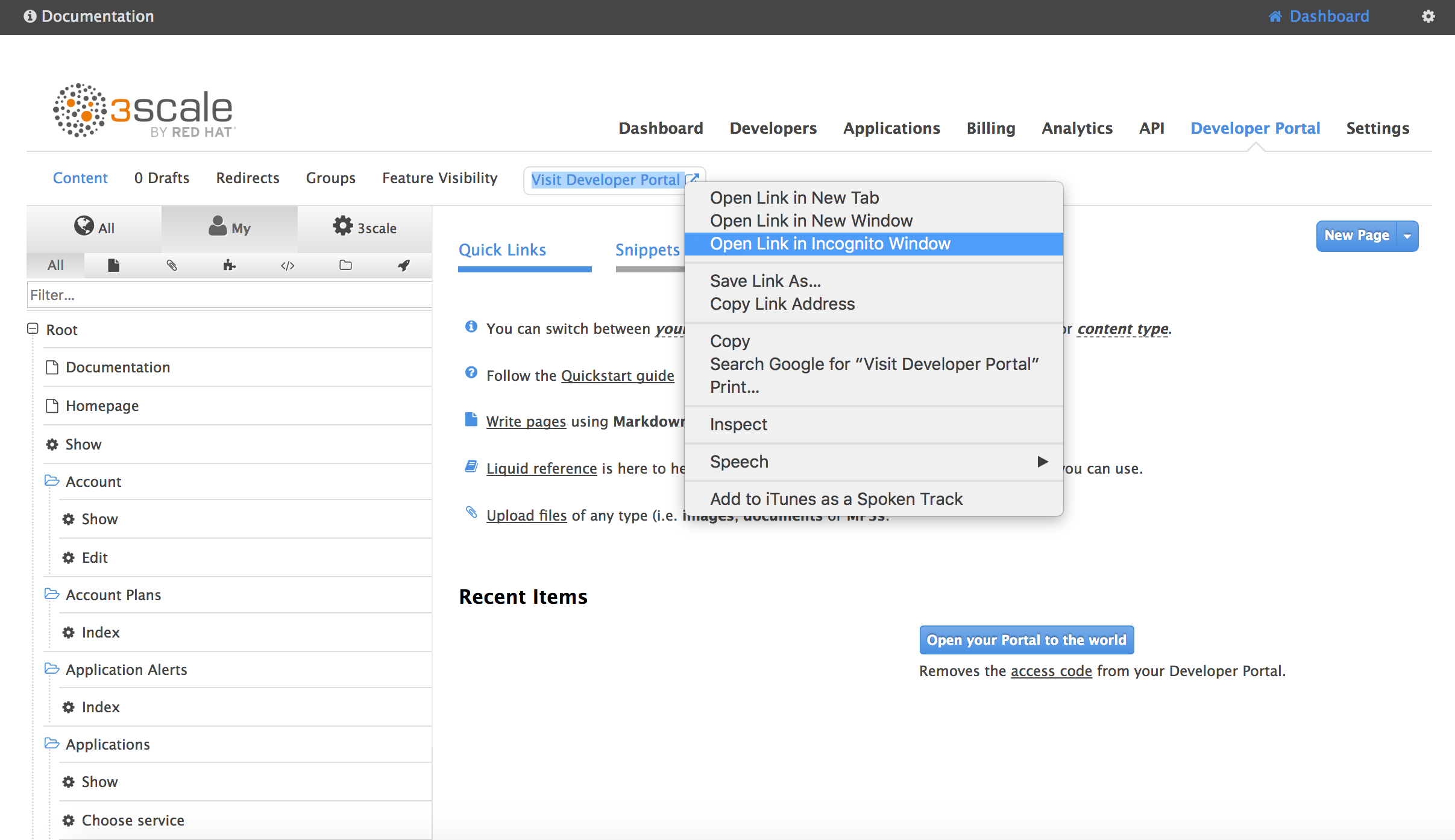
Test it out. Go to Developer Portal -> (in a new Incognito Window) Right click Visit Developer Portal - Open an Incognito Window
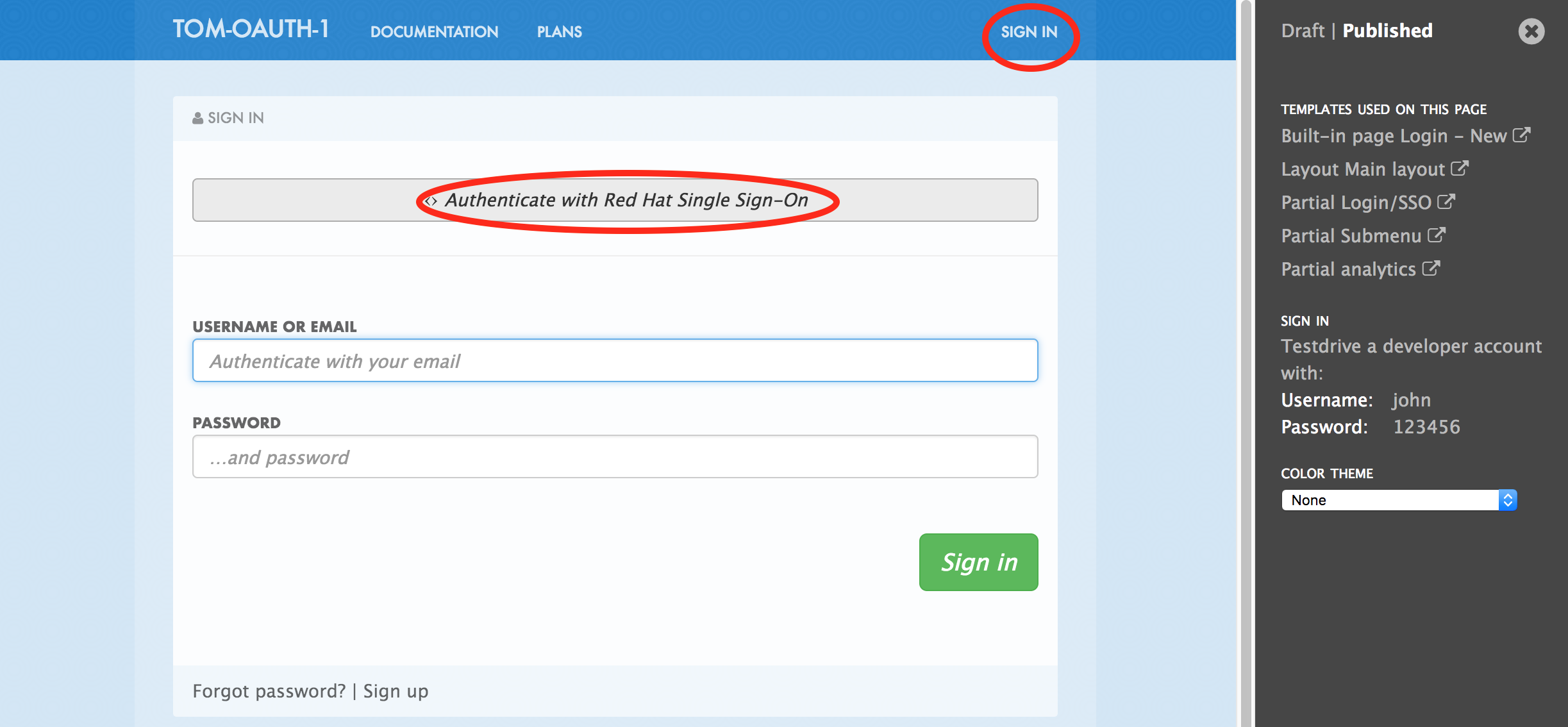
Click Sign In
Authenticate with Red Hat SSO. Use either rh-sso-ldap-user-id or rh-sso-user-id
After logging in you'll be prompted to add Custom signup fields. Do this and follow the sequence to completion. Close window
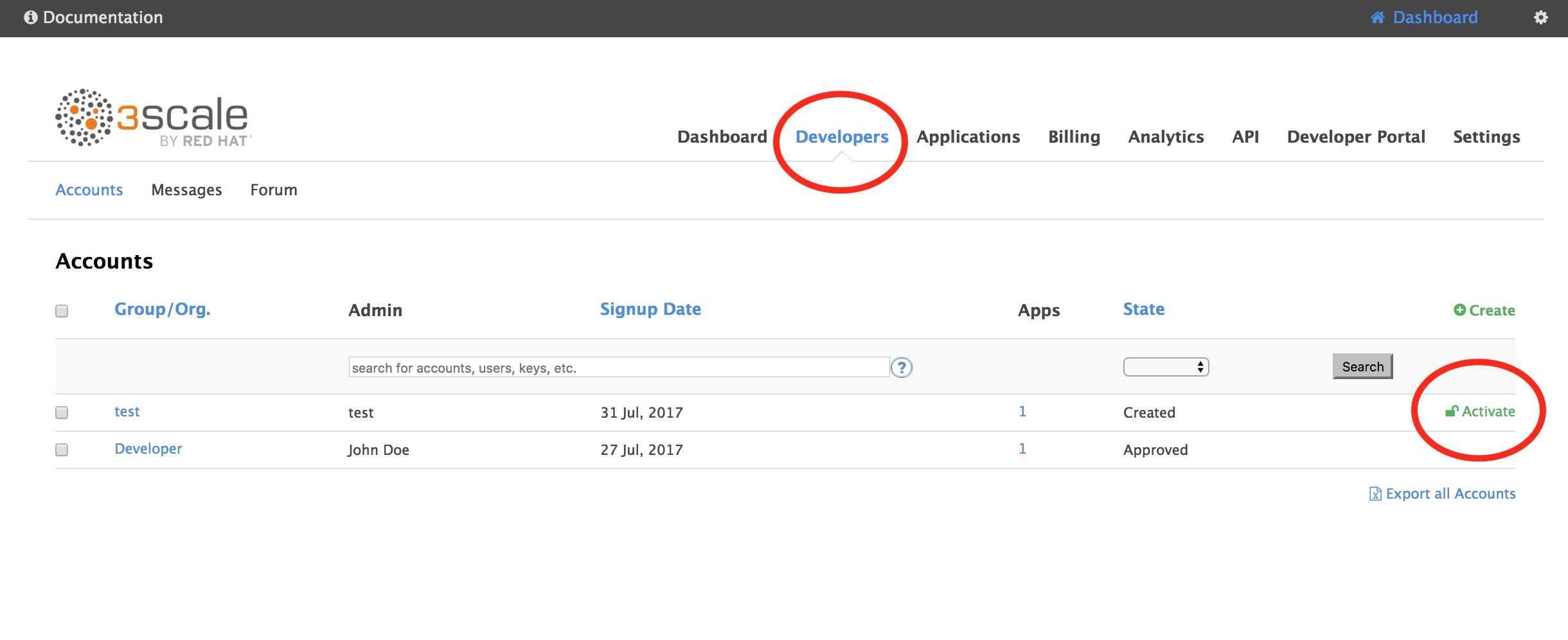
Now as your 3scale Admin user, activate this Signup Request. Go to your Developers view and click Activate:
Dev Portal signup is now complete and your Dev portal user can sign in with credentials stored in Red Hat SSO or an LDAP it brokers to.