The cyber security incident reporting portal provides a secured login for each Western Australian government agency to:
- report cyber incidents
- enable coordination of incident response
- receive updates on ongoing cyber security events and topics
All agencies should have a Cyber Incident Response Plan (ACSC Practitioner Guidance updated April 2024, pdf also available) defined that clearly outlines the work to ensure an effective response and prompt recovery in the event security controls don’t prevent an incident occurring. This plan should be tested and regularly reviewed.
ACSC also published an excellent ACSC Cyber Incident Response Plan - Word Template - March 2023 (docx) suitable for tailoring to an organisations specific context. The guidance includes some highly relevant appendices:
!!! abstract "Incident Response Appendices"
- Appendix A - Terminology and definitions
- Appendix B - Cyber Security Incident Response Readiness Checklist
- Appendix C - ASD cyber security incident triage questions
- Appendix D - Situation Report Template
- Appendix E - Cyber Security Incident Log Template
- Appendix F - Evidence Register Template
- Appendix G - Remediation Action Plan Template
- Appendix H - Post cyber security incident reviews
- Appendix I - Action Register Template
- Appendix J - Role cards
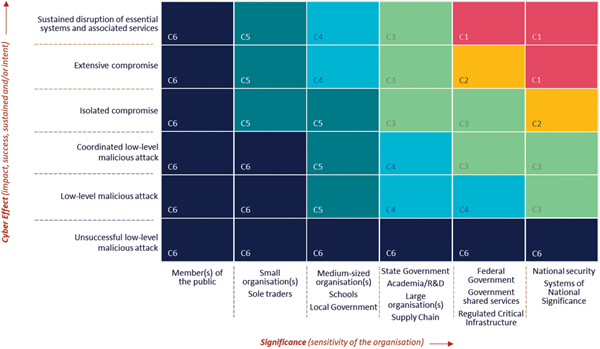
- Appendix K - ASD Cyber Security Incident Categorisation Matrix
- Agencies can request access by emailing [email protected].
- Agencies with existing access can use the Request access to the Incident Reporting Portal WASOC IRP form.
The WA Security Operations Centre - IRP is accessible using any modern browser.
When logging in you will be prompted to use Single Sign On, please do this and Continue with Microsoft for your Atlassian Identity.
- Report a cyber incident - WASOC IRP form
- Enter the details of your incident
- Select Share with your organisation
- SIEM Sentinel incidents will be automatically integrated with the IRP for monitored customers.
- To manage alerting and integrations, please use the Request Assistance WASOC IRP form
You can view all of your security teams incidents on the Requests page in the WASOC IRP.
The below actions can be taken on your incidents, noting that all standard activities (classification, severity, labeling, comments) should be able to be undertaken in your SIEM and automatically synced to the IRP.
- Search existing incidents by summary, description or entities
- Add comment/ updates to an Incident
- If you add comments in your SIEM they will sync automatically
- Attachments and Non-SIEM Incidents can be directly commented on in the portal
- Request assistance
- Create a post-incident review
- The WA SOC can review your PIR and provide additional context as needed
If your team is seeing a lot of false positive detections, please review Handle false positives in Microsoft Sentinel and reach out to the SOC using Request Assistance for further advice.
For any other SIEM advice, general security problems and questions don't hesitate to reach out to the SOC using Request Assistance. For any urgent incidents please call us on Teams or via phone.
The below aggregate statistics are being captured by the new portal and will be available in the SOC monthly reports for your organisation. Monthly reports are under review to align them to the WA Government Cyber Security Policy and the NIST Cyber Security Framework.
- Incident statistics
- Total Detections
- Triage types (automated, manual)
- True / False / Benign breakdown
- MITRE Data Sources overview (SIEM event coverage)
- MITRE TTP Detection overview (Detection Analytics coverage)